
Setting Up User Authentication
Introducing user authentication
User authentication is a method of identifying and allowing access to specified remote users dialing in over both analog and digital lines. Types of Authentication
The MAX supports these types of authentication: CLID (Calling Line ID)
You can require the MAX to authenticate incoming calls by checking the calling party's phone number. The MAX performs CLID authentication before answering an incoming call. For details on configuring the MAX for CLID authentication, see Setting up CLID authentication.
Called Number
Called Number authentication works much like CLID authentication, except that the MAX uses the number called by the remote end to authenticate the connection. The called number appears in an ISDN message as part of the call when DNIS (Dial Number Information Service) is in use. Called Number authentication is also known as DNIS authentication. Callback
Callback security instructs the MAX to hang up on an incoming caller and then immediately initiate a call to that destination. For details on configuring the MAX to use callback security, see Setting up callback security.
Name and password
You can configure the MAX to verify an incoming call based on the user's name and password; you can also specify a name and password for outgoing calls. Name and password authentication applies to these types of calls:
How does user authentication work?
All user authentication relies on the MAX finding a matching profile to verify information presented by the caller. The matching Connection profile or Name/Password profile may be resident locally; or, the profile might be managed by a third-party security server such as RADIUS, TACACS, or TACACS+.
This section describes how the MAX authenticates an incoming call. These events take place:
The CLID is the phone number of the calling device, which is not always provided by the WAN carrier. When the profile requires CLID authentication, the caller's phone number must match a phone number specified in a local Connection profile or RADIUS user profile.
If one does not exist, it then looks for a matching phone number in a RADIUS user profile. If it cannot find the correct phone number, the MAX hangs up.
Note: The RADIUS attribute Ascend-Require-Auth specifies whether additional
authentication is required. See the RADIUS Configuration Guide for more information.
If authentication succeeds using a local Connection profile, the MAX uses the parameters specified in the profile to build the connection.
If the MAX finds a Name/Password profile, it uses the name and password in the Name/Password profile and builds the connection using the settings in the Answer profile.
If authentication succeeds using a RADIUS user profile, the MAX uses the specified RADIUS attributes to build the connection. The MAX can then forward the call to its bridge/router or other destination. For example, the MAX might forward a terminal server call to a Telnet or TCP host.
For details on configuring the MAX to use a TACACS or TACACS+ server, see Setting up an authentication server. For details on configuring the MAX to use a RADIUS server, see the MAX RADIUS Configuration Guide.
For details on configuring the MAX to use a Defender server, see Configuring direct Defender server authentication.
You can set up your network site to require that users change passwords very frequently, many times per day. When you do so, you use an external authentication server, such as an ACE or SafeWord server. For details, see Chapter 3, Setting Up User Authentication.
Setting up CLID authentication
You can require the MAX to authenticate incoming calls by checking the calling party's phone number. The MAX performs CLID authentication before answering an incoming call. You can thereby ensure that the call originates from a known location. To set up CLID authentication, use the parameters listed in Table 3-2.
When you set up CLID authentication, you can choose one of these configurations:
For details, see Setting up authentication using a name, password, and calling line ID.
For details, see Setting up authentication using a calling line ID only.
When you set up CLID authentication either in RADIUS or in a MAX Connection profile, you must specify what the MAX requires for the CLID authentication. There are three options:
Setting up authentication using a name, password, and calling line ID
To require all callers to authenticate using name, password, and CLID, follow these steps:
Set CLID Timeout Busy=Yes, to specify that MAX returns User Busy as the disconnect cause when CLID authentication fails due to a RADIUS timeout.
Set CLID Fail Busy=Yes to specify that the MAX returns User Busy when CLID authentication fails to any reason other than a RADIUS timeout.
To require all callers to authenticate using a calling line ID only, follow these steps:
The Require setting indicates that the calling party's phone number must match the value of the Calling # parameter in the Connection profile before the MAX can answer the call. If CLID is not available, the MAX does not answer the call.
Setting up called number authentication
Called Number authentication works much like CLID authentication, except that the MAX uses the number called by the remote end to authenticate the connection. The called number appears in an ISDN message as part of the call when DNIS is in use. Called number authentication is also known as DNIS authentication.
Setting up called number authentication options
You can choose one of these configurations for called number authentication:
For details, see Setting up authentication using a name, password, and called number.
For details, see Setting up authentication using the called number only.
Setting up authentication using a name, password, and called number
For further information, see the RADIUS Configuration Guide.
To require all callers to authenticate using a called number only, follow these steps:
The Called Require setting indicates that the called number must match the value of the Called # parameter in the Connection profile before the MAX can answer the call. If the called number is not available, the MAX does not answer the call.
Setting up callback security
There are two types of callback security: Ascend callback security and Microsoft callback security. Ascend callback security
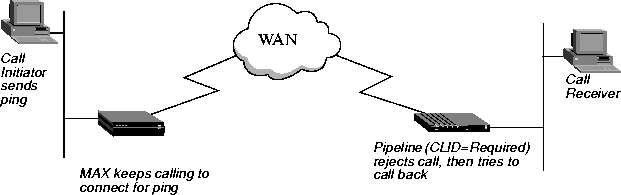
Callback security instructs the MAX to hang up on an incoming caller and then immediately initiate a call to that destination. Callback ensures that the connection is made with a known destination.
Figure 3-1. Callback connection failure
For information on setting up callback security in RADIUS, see the MAX RADIUS Configuration Guide.
For example, you might enter this setting:
Dial #=555-1213Note: The MAX can also use the CLID in order to reach the remote end of the connection, if the CLID is available.
For example, you might enter this setting:
Calling #=555-1213
Callback=YesNote: Callback does not apply to leased lines (if Call Type=Nailed).
Exp Callback=Yes
AnsOrig=Both
When you set Callback=Yes, you must also set AnsOrig=Both, because the Connection profile must both answer the call and call back the device requesting access. Similarly, the calling device must be able to both dial to and accept incoming calls from the MAX.
To prevent a problem when CLID on the called machine is set to Required, set Exp Callback to Yes.
Microsoft's Callback Control Protocol (CBCP)
Microsoft Corporation developed CBCP to address a need for greater security with PPP connections. The standardized callback option defined in RFC 1570 has a potential security risk because the authentication is performed after the callback. CBCP callback like Ascend's proprietary callback, occurs after authentication, leaving no potential security hole. Ascend's implementation of CBCP
CBCP is an option negotiated during the LCP negotiation of a PPP session. While support for CBCP is configured system-wide on the MAX, not every connection must negotiate its use. Parameters exist in the Answer Profile under Ethernet > Answer > PPP Options, and to each Connection Profile under Ethernet > Connections > Any Connection profile > Encaps Options. The calling and called sides of a PPP session initiate authentication after acknowledging that CBCP is to be used.
The MAX employs the user name and password to link a caller with a specific Connection profile or RADIUS User profile. Configured CBCP parameters in that Connection profile specify variables for the callback. If, at any point, the client and the MAX disagree about any CBCP variables, the MAX might drop the connection.
For information on setting up callback security in RADIUS, see the MAX RADIUS Configuration Guide.
Negotiation of CBCP
Following are the steps from initial connection to MAX callback:
Caller and MAX must agree to use CBCP. Otherwise, the MAX terminates the connection.
The client also supplies to the MAX the number of seconds it should delay before initiating the callback, and, if applicable, the phone number.
Setting up call authentication via serial AIM ports
You can specify a password for calls placed across the Host serial inverse multiplexing ports in the Call profile for outgoing calls and in the Port configuration profile for incoming calls. Understanding serial call authentication
Authentication is used only if the receiving unit has a password defined in the Port profile. If the Port profile in the receiving unit does not have a password defined, the units connect without authentication even though the originating unit may have sent authentication parameters.
Upon initial connection of the first channel, the originating unit passes the Call profile password to the authenticating unit. The authenticating unit compares the password received with that stored in the Port configuration profile. If the password received matches the stored password, the session is established normally for the remainder of the call. If there is no match, the authenticating unit sends a message back to the originator and drops the session. The port status screen in Host > Dual\>portname\>Message Log indicates that the call failed authentication.
Configuring serial port passwords
To set the passwords, follow these steps:
Dynamic Bandwidth Allocation (DBA) enables the MAX to increase bandwidth as needed and drop bandwidth when it is no longer required.
Setting up authentication of PPP, MP, and MP+ calls
The answering unit always determines the authentication method to use for the call. You can specify PAP, CHAP, or MS-CHAP authentication for name and password verification of incoming PPP, MP, or MP+ calls.
This section describes the following tasks:
ftp://ftp.microsoft.com/DEVELOPR/RFC/chapexts.txt
For complete information on setting up PPP, MP, and MP+ calls on the MAX, see the MAX ISP & Telecommuting Configuration Guide. For complete information on setting up PPP, MP, and MP+ calls and authentication in RADIUS, see the RADIUS Configuration Guide.
Understanding PPP, MP, and MP+
PPP enables you to set up a single-channel connection to any other device running PPP. A PPP connection can support IP routing, IPX routing, protocol-independent bridging, and password authentication using PAP, CHAP, or MS-CHAP.
Figure 3-2. A PPP connection
An MP+ connection can combine up to 30 channels into a single high-speed connection.
Figure 3-3. An MP+ connection
Understanding PAP, CHAP, and MS-CHAP
Keep this information in mind:
For PAP authentication, these events take place:
For CHAP authentication, these events take place:
No encryption is necessary, because MD5 creates a one-way code that cannot be decoded. In addition, RADIUS cannot extract the remote secret. Therefore, it cannot provide a password to a UNIX password system; for this reason, CHAP and UNIX authentication cannot work together.
ftp://ftp.microsoft.com/DEVELOPR/RFC/chapexts.txt
Setting system-wide parameters
To set system-wide parameters for PAP, CHAP, or MS-CHAP authentication, follow these steps:
This setting specifies that the MAX rejects incoming calls for which it can find no Connection profile, no Name/Password profile, and no entry on a remote authentication server.
Note: PAP, CHAP, and MS-CHAP authentication is available only if you choose MP,
MPP, or PPP.
When you specify Either, the MAX allows authentication if the remote peer can authenticate using any of the designated authentication schemes. If you specify a protocol, the MAX allows authentication only if the remote peer uses that protocol for authentication.
Unlike Connection profiles and RADIUS user profiles, Name/Password profiles cannot specify an IP address for the calling station. When you use a Name/Password profile to authenticate an IP routing connection, the MAX automatically assigns the PPP caller a dynamic IP address as the connection is established. For a call configured in a Name/Password profile, the address assignment is always from the pool of addresses defined as Pool #1, if Pool #1 exists and has available addresses. If Pool #1 does not exist or does not have available addresses, the MAX assigns an address from Pool #2.
The Pool #n Count parameter specifies the number of IP addresses in the IP address pool. Specify a number between 0 and 254. The default value is 0 (zero).
The Pool Only parameter determines whether a caller can reject an IP address assignment and use his or her own IP address. To eliminate the possibility of a caller rejecting the automatic dynamic assignment and spoofing a local, trusted address, set Pool Only=Yes when using Name/Password profiles to authenticate IP routing connections.
To set Connection profile parameters for PAP, CHAP, or MS-CHAP authentication, follow these steps:
If the password specified by Recv PW does not match the remote end's value for Send PW (in a Connection profile), Ascend-Send-Passwd (in a RADIUS user profile), or Ascend-Send-Passwd (in a RADIUS user profile), the MAX disconnects the link.
The Name/Password profile applies only to ARA, PPP, MP, and MP+ calls and to terminal server users.
To set Name/Password profile parameters for PAP, CHAP, or MS-CHAP authentication, follow these steps:
In a Name/Password profile, the Name parameter specifies the username associated with the profile; the name you specify also becomes the name of the profile.
If the password specified by Recv PW does not match the remote end's value for Send PW (in a Connection profile), Ascend-Send-Passwd (in a RADIUS user profile), or Ascend-Send-Passwd (in a RADIUS user profile), the MAX disconnects the link.
For example, you can set up a Connection Profile for the Sales group to use when dialing in, then set up a Name/Password Profile for each individual salesperson. To prevent a user (or users) from dialing in using one of the two following methods:
To specify PAP, CHAP, or MS-CHAP for an outgoing PPP, MP, or MP+ call, follow these steps:
This parameter specifies the authentication protocol that the MAX requests when initiating a connection using PPP, MP, or MP+ encapsulation. The answering side of the connection determines which authentication protocol the connection uses (if any).
If the password specified by Send PW does not match the remote end's value for Recv PW (in a Connection profile) or Ascend-Receive-Secret (in a RADIUS user profile), the remote end disconnects the link.
Setting up authentication for dial-in terminal server users
This section describes the authentication of users calling into the MAX from a terminal or other device that transmits and receives asynchronous data.These sessions are called remote terminal server sessions even if the user never sees the MAX terminal server commands or menu.
How terminal server authentication works
More general information on how authentication works in the MAX is in How does user authentication work?. See"Per-user terminal server authentication" for the differences between standard terminal server authentication and per-user terminal server authentication, such as CLID and Called-party authentication.
Standard terminal server authentication
Terminal server authentication makes use of these parameters and profiles:
The CLID is the phone number of the calling device, which is not always provided by the WAN carrier. When the profile requires CLID authentication, the caller's phone number must match a phone number specified in a local Connection profile or RADIUS user profile.
If one does not exist, it then looks for a matching phone number in a RADIUS user profile. If it cannot find the correct phone number, the MAX hangs up.
Modem calls
A modem call may contain PPP encapsulation. For example, if the user is running Windows 95 with the TCP/IP stack and Netscape, Windows 95 could be configured to dial up the MAX whenever Netscape is started. In that case, Windows 95 would be running async PPP. After the call is forwarded to the terminal server software, if PPP encapsulation is detected, the call is forwarded to the bridge/router software for an async PPP session.
This section describes first-level authentication using the Passwd parameter. For information on authentication using a Connection profile, see Setting Connection profile parameters.
Dial-in calls with no login host specified
You can configure the MAX to accept dial-in calls when Login-Service=TCP-CLEAR or Login-Service=Telnet, and no Login Host is specified in the RADIUS users profile. This does not apply to PPP encapsulated calls, since the MAX does not accept dial-in PPP calls with the Login-Service set either to Telnet or TCP-CLEAR. Immediate Service
You can specify that a remote terminal server user can establish a Telnet session immediately after the terminal server banner appears. To do this, set Immed Service=Telnet and Telnet Host Auth=Yes in Ethernet > Mod Config > TServ Options menu. Configuring terminal server authentication
Table 3-11 lists the parameters you can use to set up terminal server password authentication.
To set up password authentication for the terminal server interface, follow these steps:
This setting enables users to access the terminal server interface. If you set this parameter to No, no one can access the terminal server interface.
You can enter up to 20 characters. The password is case sensitive
The Security parameter specifies whether a user must enter a password under different circumstances.
Specify the number of seconds the MAX waits for a user to complete logging in before disconnecting the user in the Login Timeout field.
Specify the prompt the terminal server displays when asking the user for a login name.
Specify the prompt the terminal server displays when asking the user for a password.
If you prefer, you can authenticate a terminal server user with the name and password from a profile constructed a name and password from the Name/Password profile, with any additional required parameter settings from the Answer or Connection profile. Since the Name/Password profile does not supply all the parameters a terminal server session might need, the MAX uses the settings from the Answer profile or Connection profile named in the Template parameter for these additional parameters.
These parameters specify the IP addresses and descriptions of the first, second, third, and fourth hosts to which an operator can Telnet. The user sees a list of hosts only if he or she has access to the menu-driven interface. For details on granting this access, see Restricting Telnet, raw TCP, and Rlogin access to the terminal server.
For example, you might make these settings:
Host #1 Addr=10.2.3.1/24
Host #1 Text=host1.abc.com
Host #2 Addr=10.2.3.2/24
Host #2 Text=host2.abc.com
Host #3 Addr=10.2.3.3/24
Host #3 Text=host3.abc.com
Host #4 Addr=10.2.3.4/24
Host #4 Text=host4.abc.comThe MAX ignores the Host #n Addr parameter if a RADIUS server supplies the list of Telnet hosts-that is, if you set Remote Conf=Yes. For information on setting up a list of hosts in RADIUS, see the MAX RADIUS Configuration Guide.
Setting up Combinet authentication
The MAX supports Combinet bridging to link two LANs as though they were one segment. Figure 3-4 shows a Combinet connection between two networks.
Figure 3-4. A Combinet connection
Table 3-12 lists the Combinet authentication parameters.
This section describes how to set up authentication for Combinet calls in the MAX configuration interface. For complete information on setting up Combinet calls on the MAX, see the MAX ISP & Telecommuting Configuration Guide. For information on setting up Combinet calls and Combinet authentication in RADIUS, see the MAX RADIUS Configuration Guide.
Understanding Combinet authentication
To configure incoming connections using Combinet authentication, you must carry out these tasks:
If it cannot find a matching Connection profile, the MAX looks for a RADIUS user profile, a TACACS profile, or a TACACS+ profile.
Note that Combinet does not support PAP, CHAP, or MS-CHAP authentication.
To set Connection profile parameters for authenticating a Combinet connection, follow these steps:
You can specify between 1 and 1440 minutes. The connection is checked once per minute, so the actual time of the call is slightly longer (usually less than a minute longer) than the actual time you set.
The Recv PW parameter specifies the password that the remote end of the link must send;
For more information on restricting the Immediate Modem feature, seeRestricting access to the Immediate Modem feature.
Setting up ARA authentication
ARA connections rely on AppleTalk; the MAX includes a minimal AppleTalk stack for ARA support. The minimal stack includes an NBP (Name Binding Protocol) network visible entity and an AEP (AppleTalk Echo Protocol) echo responder; you can therefore use standard AppleTalk management and diagnostic tools, such as InterPoll from Apple Computer, to obtain information.
Figure 3-5 shows a Macintosh with an internal modem dialing into the MAX. The Macintosh uses the ARA Client software to communicate with an IP host on the Ethernet.
Figure 3-5. An ARA connection
This section describes how to set up ARA authentication in the MAX configuration interface. For complete information on setting up ARA calls on the MAX, see the MAX ISP & Telecommuting Configuration Guide. For complete information on setting up ARA calls and authentication in RADIUS, see the MAX RADIUS Configuration Guide.
Understanding ARA authentication
To configure incoming connections using ARA authentication, you must carry out these tasks:
If it cannot find a matching Connection profile, the MAX looks for a Name/Password profile. If it cannot find a matching Name/Password profile, the MAX looks for a RADIUS user profile, TACACS profile, or TACACS+ profile.
Note that ARA does not support PAP, CHAP, or MS-CHAP authentication.
Unlike Connection profiles and RADIUS user profiles, Name/Password profiles cannot specify an IP address for the calling station. When you use a Name/Password profile to authenticate an IP routing connection, the MAX automatically assigns the PPP caller a dynamic IP address as the connection is established. For a call configured in a Name/Password profile, the address assignment is always from the pool of addresses defined as Pool #1, if Pool #1 exists and has available addresses. If Pool #1 does not exist or does not have available addresses, the MAX assigns an address from Pool #2.
The Pool #n Count parameter specifies the number of IP addresses in the IP address pool. Specify a number between 0 and 254. The default value is 0 (zero).
The Pool Only parameter determines whether a caller can reject an IP address assignment and use his or her own IP address. To eliminate the possibility of a caller rejecting the automatic dynamic assignment and spoofing a local, trusted address, set Pool Only=Yes when using Name/Password profiles to authenticate IP routing connections.
To set Connection profile parameters for ARA authentication, follow these steps:
The Name/Password profile applies only to ARA (AppleTalk Remote Authentication) and PPP-encapsulated calls. It does not apply to terminal server users.
In a Name/Password profile, the Name parameter specifies the username associated with the profile; the name you specify also becomes the name of the profile.
If the password specified by Recv PW does not match the remote end's value for Send PW (in a Connection profile), Ascend-Send-Passwd (in a RADIUS user profile), or Ascend-Send-Secret (in a RADIUS user profile), the MAX disconnects the link.
For example, you can set up a Connection Profile for the Sales group to use when dialing in, then set up a Name/Password Profile for each individual salesperson. To prevent a user (or users) from dialing in using one of the two following methods:
The SecurID client module must be version 1.3 or later.
Once the user makes the initial connection, SecurID authentication begins with a pop-up screen on the Macintosh. At this point, the user must enter the User ID and Passcode. When Auth=LOGOUT/RADIUS, the username must be SecurID, and there no password should be given. If the user enters incorrect values, he or she gets two more tries to authenticate before the connection fails.
If the user is required to enter a new PIN, a pop-up screen prompts for this information. The user has three chances to enter the correct PIN. Once the new PIN is accepted, a pop-up screen instructs the Macintosh user to wait for the token code to change and then to log in with the new PIN and token code.
Setting up X.25 authentication
X.25 is an international standard protocol established by the Consultative Committee on International Telephony and Telegraphy (CCITT) to transmit information between users over a WAN. It handles both high-volume data transfers and interactive use of host machines.
This section describes how to set up X.25 authentication in the MAX configuration interface. For complete information on setting up X.25 connections on the MAX, see the MAX ISP & Telecommuting Configuration Guide. For complete information on setting up X.25 calls and authentication in RADIUS, see the MAX RADIUS Configuration Guide.
Setting up IP addressing
When a call comes in and password authentication is required, the MAX attempts to match the caller's name and password to a local Connection profile. If password authentication is not required, the MAX can match IP-routed PPP calls using the IP address specified by the Connection profile. The address can be a static address or a dynamic address.
A dynamic address comes from the pool of addresses set by the Pool #n Start and Pool #n Count parameters or by the Ascend-IP-Pool-Definition attribute.
If the calling station accepts the IP address, the MAX authenticates the connection using PAP, CHAP, or MS-CHAP, and then establishes the connection. If the calling station does not accept the IP address assignment, the MAX ends the call without completing PAP, CHAP, or MS-CHAP authentication.
The sections that follow describe how to carry out these tasks:
When you specify this setting, the MAX asks the device to accept an assigned address, choosing an address from the pool of addresses set by the Pool #n Start and Pool #n Count parameters or by the Ascend-IP-Pool-Definition attribute. If the calling end accepts the IP address, the MAX sets the LAN Adrs parameter in the Connection profile to the assigned address.
The Pool #n Count parameter specifies the number of IP addresses in the IP address pool. Specify a number between 0 and 254. The default value is 0 (zero).
When you specify this setting, the MAX asks the device to accept an assigned address, choosing an address from the pool of addresses set by the Pool #n Start and Pool #n Count parameters or by the Ascend-IP-Pool-Definition attribute. If the calling end accepts the IP address, the MAX sets the LAN Adrs parameter in the Connection profile to the assigned address.
The Pool #n Count parameter specifies the number of IP addresses in the IP address pool. Specify a number between 0 and 254. The default value is 0 (zero).
This setting requires the calling station to accept the static address specified in a Connection profile or RADIUS user profile, or a dynamic address. If the calling station rejects the assignment, the MAX ends the call.
Unlike Connection profiles and RADIUS user profiles, Name/Password profiles cannot specify an IP address for the calling station. When you use a Name/Password profile to authenticate an IP routing connection, the MAX automatically assigns the PPP caller a dynamic IP address as the connection is established, ensuring that the user is not spoofing the address. Table 3-16 shows the relevant parameters on the MAX.
To set parameters to prevent IP spoofing, follow these steps:
In a Name/Password profile, the Name parameter specifies the username associated with the profile; the name you specify also becomes the name of the profile.
If the password specified by Recv PW does not match the remote end's value for Send PW, the MAX disconnects the link.
The Pool #n Count parameter specifies the number of IP addresses in the IP address pool. Specify a number between 0 and 254. The default value is 0 (zero).
The Pool Only parameter determines whether a caller can reject an IP address assignment and use his or her own IP address. To eliminate the possibility of a caller rejecting the automatic dynamic assignment and spoofing a local, trusted address, set Pool Only=Yes when using Name/Password profiles to authenticate IP routing connections.
Setting up an authentication server
The MAX supports resident Connection profiles and Name/Password profiles for authenticating incoming connections, but the total number of supported profiles is limited by the amount of RAM in the unit. Many ISPs and other large sites use a third-party authentication server such as RADIUS (Remote Authentication Dial In User Service), TACACS (Terminal Access Concentrator Access Control Server), or TACACS+ (Terminal Access Concentrator Access Control Server Plus) to centrally control, manage, and audit security. Understanding authentication servers
When the MAX receives an incoming call, it first looks through its resident profiles (Connection and Name/Password profiles). If it does not find a matching profile, it checks its Ethernet profile for an authentication server's address. If it finds one, it accesses the authentication database in that server to search for a matching profile. The MAX supports these types of authentication servers:
RADIUS is a protocol originally developed by Livingston Enterprises, and extended by Ascend Communications, Inc. The extensions provided by Ascend let you configure most of the features supported by the resident profiles. The information resides in a database on a PC or UNIX system; the RADIUS daemon on that system accesses the data.
TACACS is a simple query/response protocol that enables the MAX to check a user's password and enable or prevent access. TACACS supports PAP (Password Authentication Protocol), Combinet name and password validation, and terminal server validation. It does not support CHAP authentication.
TACACS+ is an extension of TACACS. For information on setting up the MAX to operate with a TACACS+ server, see Configuring the MAX to use a TACACS or TACACS+ server.
This section describes how to configure the MAX to communicate with a TACACS or TACACS+ server. Follow these steps:
X0-X00 Mod Config
Auth...
>Auth=TACACS
Auth Host #1=10.23.45.11
Auth Host #2=10.23.45.12
Auth Host #3=10.23.45.13
Auth Port=1645
Auth Timeout=5
Auth Key=N/A
Auth Pool=N/A
Auth Req=Yes
Local Profile First=Yes
APP Server=No
APP Host=N/A
APP Port=N/A
CLID Timeout Busy=No
CLID Fail Busy=No
SecurID DES encryption=N/A
SecurID host retries=N/A
SecurID NodeSecret=N/A
You can specify up to three addresses. The MAX first tries to connect to Auth Host #1; if it receives no response within the time specified by the Auth Timeout parameter, it tries again to connect to to Auth Host #1 and waits for the same amount of time. If the MAX does not receive a response within the specified timeout, it sends a request for authentication to Auth Host #2; if it again receives no response within the time specified by Auth Timeout, it tries to connect to the next server on the Auth Host List and repeats the process. If the MAX unit's request again times out, it reinitiates the process with Auth Host #1. The MAX can complete this cycle of requests a maximum of ten times. If the MAX is unsuccessful in obtaining a response from any of the servers on the list, the connection fails.
For example, you might specify this setting:
Auth Port=1645The MAX and the TACACS or TACACS+ software must agree about which UDP port to use for communication, so make sure that the number you specify for the Auth Port parameter matches the number specified in the TACACS or TACACS+ configuration file.
If the MAX does not receive a response within the time specified by Auth Timeout, it sends the authentication request to the next authentication server specified by the Auth Host parameter.
If you enter No, remote authentication is tried first. The MAX waits for authentication to succeed or for the timeout specified in Auth Timeout to expire. This can take longer than the timeout specified for the connection and causes all connection attempts to fail.
Type a port number between 0 and 65535. The default value is 0 (zero); if you accept this value, the Ascend unit can use any port number between 1024 and 2000.
Copyright © 1998, Ascend Communications, Inc. All rights reserved.