
Introduction to Ascend filters
A packet filter contains rules that specifies what the MAX does when it encounters different types of packets. When you specify a packet filter in a RADIUS user profile, the MAX monitors the data stream associated with that profile and takes a specified action when packet contents match the filter rules. Each filter specification either forwards or drops packets. You can apply a filter to inbound packets, outbound packets, or both. In addition, you can specify that the MAX forward or drop those packets that match the rules, or all packets except those that match the rules.
A match occurs at the first successful comparison between a filter and the packet being examined. When a comparison succeeds, the filtering process stops and the MAX applies the forward or drop action to the packet.
If no comparisons succeed, the packet does not match the filter. However, the MAX does not forward the packet. When no filter is in use, the MAX forwards all packets. However, once you apply a filter to a connection, this default is reversed. For security purposes, the MAX does not automatically forward non-matching packets. It requires a rule that explicitly allows those packets to pass.
In a generic filter, all settings work together to specify a location in a packet and a number that the MAX compares to the value in that location. In an IP filter, the MAX makes a set of distinct comparisons in order. When a comparison fails, the packet goes on to the next comparison. When a comparison succeeds, the filtering process stops and the MAX applies the forward or drop action to the packet. The IP filter tests proceed in the following order:
If no comparisons succeed, the packet does not match the filter and the MAX does not forward the packet. When no filter is in use the MAX forwards all packets. Once you aply a filter to a connection, this default is reversed. For security purposes, the MAX does not automatically foward non-matching packets. It requires a rule that explicitly allows these packets to pass. Packets can pass through more than one filter. If both a data filter and call filter apply to an interface, the data filter is applied first.
When you define a filter in a user profile, it applies to data the user sends or receives. If you make changes to a filter or filter reference in a RADIUS user profile, the changes do not take effect until a call uses that profile. For complete information about how filters work, see the chapter on using filters in the MAX ISP and Telecommuting Configuration Guide.
You can also set up filters on the MAX or define firewalls in SAM, and then specify those filters or firewalls in a RADIUS user profile. When the connection is made the RADIUS user profile determines which filters are used for the connection. For more information, see the MAX RADIUS Configuration Guide, or your SAM documentation.
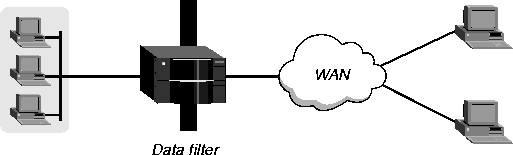
Data filters for dropping or forwarding certain packets
A data filter defines which packets the MAX can transmit on a connection. Many sites use data filters for security purposes, but you can apply data filters to any purpose that requires the MAX to drop or forward only specific packets. For example, you can use data filters to drop packets addressed to particular hosts or to prevent broadcasts from going across the WAN. You can also use data filters to allow users to access only specific devices across the WAN.
Figure 4-1. Data filters can drop or forward certain packets
Overview of filter profiles
Figure 4-2 shows how filters are organized adn the terminology used to describe each part of a filter.
Figure 4-2. Filter terminology
At the top level of a Filter profile are submenus labeled Input Filters and Output Filters. Each submenu contains a list of 12 filters. The MAX applies the conditions you define within the filters to the inbound or outbound packet stream in order, from 1 to 12. See Filtering inbound and outbound packets for details.
Each input filter or output filter can be one of two types: Generic or IP, or IPX.
Filter conditions specify the actual packet characteristics that the MAX examines in the data stream. Generic filter conditions specify locations and values that can appear in any packet. IP filter conditions specify IP-specific packet characteristics, such as address, mask, and port. IPX filter conditions specify IPX-specific packet characteristics, such as network address, node address, and socket number. Once you assign a type, you can open the corresponding submenu to define the packet-level filter conditions. For details, see Defining generic filter conditions and Defining IP filter conditions.
Filtering inbound and outbound packets
To set up filters, you must complete the following tasks:
Name=IP Data
When you select Input Filters, the following menu appears:
50-401 IP DataYou can specify up to 12 input filters and 12 output filters in a Filter profile. The MAX applies these filters in the order in which they appear; a filter must be activated for the MAX to apply it. Input filters cause the MAX to examine incoming packets. Output filters cause the MAX to examine outgoing packets.
Input filters...
>In filter 01
In filter 02
In filter 03
In filter 04
In filter 05
In filter 06
In filter 07
In filter 08
In filter 09
In filter 10
In filter 11
In filter 12
If the MAX applies the filter as a data filter on Ethernet, it affects packets from the Ethernet into the MAX or from the MAX out to the Ethernet. If the MAX applies a data filter on a WAN interface defined in a Connection profile, the filter affects packets from that WAN interface into the MAX or from the MAX out to that interface.
The default action is to forward packets, so if a packet does not match any of the defined conditions, the MAX simply forwards it. If you define only input filters, the default action for output filters is to forward all packets. The same is true in the other direction; if you define only output filters, the default action for inbound packets is to forward them.
When you open an "In filter," a menu like this one appears:
50-401 IP DataFor example, when you open an Out filter, the following menu appears:
In filter 01
>Valid=Yes
Type=GENERIC
Generic...
IP...
IPX...
50-401 IP Data
Out filter 01
>Valid=Yes
Type=GENERIC
Generic...
IP...
IPX...
To be able to apply the filter, you must activate it.
To specify generic filter conditions, follow these steps:
The Forward setting determines which packets the MAX transmits and receives.
The Length parameter indicates the number of bytes in a packet. The Offset parameter specifies the starting position of the bytes the filter examines; the MAX ignores the portion of the packet that exceeds the Length specification. In other words, the Offset parameter hides the left-most bytes of data, while the Length parameter hides the right-most bytes of data.
An IP filter can examine source address, destination address, and IP protocol type and port. Table 4-2 shows the filter conditions you can specify in an IP filter.
To specify IP filter conditions, follow these steps:
The Forward setting determines which packets the MAX transmits and receives.
This parameter specifies the address to which the MAX compares a packet's source address. Enter the address in dotted decimal format. The null address (0.0.0.0) is the default. If you accept the default, the MAX does not use the source address as a filtering criterion.
This parameter specifies the bits the MAX should mask when comparing a packet's source address to the value of the Src Adrs parameter. A mask hides the part of a number that appears behind each binary 0 (zero) in the mask; the MAX uses only the part of a number that appears behind each binary 1 for comparison. The MAX applies the mask to the address using a logical AND after both mask and address translated into binary format.
This parameter specifies the address to which the MAX compares a packet's destination address. Enter the address in dotted decimal format. The null address (0.0.0.0) is the default. If you accept the default, the MAX does not use the destination address as a filtering criterion.
This parameter specifies the bits the MAX should mask when comparing a packet's destination address to the value of the Dst Adrs parameter.
This parameter specifies the port number to which the MAX compares the packet's source port number. The Src Port Cmp criterion determines how the MAX carries out the comparison.
This parameter specifies the port number to which the MAX compares the packet's destination port number. The Dst Port Cmp criterion determines how the MAX carries out the comparison.
This parameter specifies the type of comparison the MAX makes when using the Dst Port # parameter. You can specify any of the settings available for Src Port Cmp (as described in step 8).
The Dst Port Cmp parameter works only for TCP and UDP packets. You must set Dst Port Cmp=None if the Protocol parameter is not set to 6 (TCP) or 17 (UDP).
The TCP Estab parameter does not apply if the Protocol field is set to any value other than 6 (TCP).
An IPX filter can examine network address, node address, and socket number. Table 4-2 shows the filter conditions you can specify in an IPX filter.
To specify IPX filter conditions, follow any or all of these steps:
Determines which packets the MAX transmits and receives.
Specifies the address to which the MAX compares a packet's source network address. Enter the address in hexadecimal format. The null address (000000000000) is the default. If you accept the default, the MAX does not use the source network address as a filtering criterion.
Specifies the address to which the MAX compares a packet's destination network address. Enter the address in hexadecimal. The null address (000000000000) is the default. If you accept the default, the MAX does not use the destination nework address as a filtering criterion.
Specifies the node address to which the MAX compares a packet's source node address. Enter the address in hexadecimal. The null address (000000000000) is the default. If you accept the default, the MAX does not use the source node address as a filtering criterion.
Specifies the node address to which the MAX compares a packet's source node address. Enter the address in hexadecimal. The null address (000000000000) is the default. If you accept the default, the MAX does not use the destination node address as a filtering criterion.
This parameter identifies a specific IPX socket. For example, 0451is the socket used for NetWare file services.
This parameter specifies the type of comparison the MAX makes when using the Src Socket # parameter.
This parameter identifies a specific IPX socket. For example, 0451is the socket used for NetWare file services.
When you set Data Filter to 0 (zero), the MAX forwards all data packets.
When you set Filter to 0 (zero), the MAX forwards all data packets.
Sample filters
This section provides a step-by-step examples of creating Filter profiles and defining IP filters for network security purposes. A sample IP filter to prevent address spoofing
IP address spoofing is a technique in which outside users pretend to be from the local network in order to obtain unauthorized access. This section shows how to define an IP data filter whose purpose is to prevent spoofing of local IP addresses. You can also use Password profiles to prevent IP address spoofing; for details, see Using Name/Password profiles to prevent IP address spoofing.
In this example, the filter first defines input filters that drop packets whose source address is on the local IP network or the loopback address (127.0.0.0). In effect, these filters say: "If you see an inbound packet with one of these source addresses, drop the packet." The third input filter defines every other source address (0.0.0.0) and specifies "Forward everything else to the local network."
50-400 Filters
50-401 IP Data
50-402 NetWare Data
50-403 AppleTalk Data
>50-404
50-405
50-406
50-407
50-408
50-409
50-410
50-411
50-412
Name=no spoofing
50-404
>Name=no spoofing
Input filters...
Output filters...
50-404
In filter 01
>Valid=Yes
Type=IP
Generic...
IP...
Ip...
>Forward=NoThe Src Mask parameter specifies the local netmask The Src Adrs parameter specifies the local IP address. If an incoming packet has the local address, the MAX does not forward it onto the Ethernet.
Src Mask=255.255.255.192
Src Adrs=192.100.50.128
Dst Mask=0.0.0.0
Dst Adrs=0.0.0.0
Protocol=0
Src Port Cmp=None
Src Port #=N/A
Dst Port Cmp=None
Dst Port #=N/A
TCP Estab=N/A
Ip...These conditions specify the loopback address in the Src Mask and Src Adrs fields. If an incoming packet has this address, the MAX does not forward it onto the Ethernet.
>Forward=No
Src Mask=255.0.0.0
Src Adrs=127.0.0.0
Dst Mask=0.0.0.0
Dst Adrs=0.0.0.0
Protocol=0
Src Port Cmp=None
Src Port #=N/A
Dst Port Cmp=None
Dst Port #=N/A
TCP Estab=N/A
Ip...These conditions specify every other source address (0.0.0.0) If an incoming packet has any non-local source address, the MAX does not forward it onto the Ethernet.
>Forward=Yes
Src Mask=0.0.0.0
Src Adrs=0.0.0.0
Dst Mask=0.0.0.0
Dst Adrs=0.0.0.0
Protocol=0
Src Port Cmp=None
Src Port #=N/A
Dst Port Cmp=None
Dst Port #=N/A
TCP Estab=N/A
Ip...The Src Mask parameter specifies the local netmask The Src Adrs parameter specifies the local IP address. If an outgoing packet has a local source address, the MAX forwards it.
>Forward=Yes
Src Mask=255.255.255.192
Src Adrs=192.100.40.128
Dst Mask=0.0.0.0
Dst Adrs=0.0.0.0
Protocol=0
Src Port Cmp=None
Src Port #=N/A
Dst Port Cmp=None
Dst Port #=N/A
TCP Estab=N/A
In this example, the local network supports a Web server and the administrator needs to carry out these tasks:
The sample data filter appears in Connection profiles. Each input filter is defined in this way:
In filter 01...Ip...Forward=Yes
In filter 01...Ip...Src Mask=0.0.0.0
In filter 01...Ip...Src Adrs=0.0.0.0
In filter 01...Ip...Dst Mask=255.255.255.255
In filter 01...Ip...Dst Adrs=192.9.250.5
In filter 01...Ip...Protocol=6
In filter 01...Ip...Src Port Cmp=None
In filter 01...Ip...Src Port #=N/A
In filter 01...Ip...Dst Port Cmp=Eql
In filter 01...Ip...Dst Port #=80
In filter 01.Ip...TCP Estab=No
In filter 02...Ip...Forward=Yes
In filter 02...Ip...Src Mask=0.0.0.0
In filter 02...Ip...Src Adrs=0.0.0.0
In filter 02...Ip...Dst Mask=0.0.0.0
In filter 02...Ip...Dst Adrs=0.0.0.0
In filter 02...Ip...Protocol=6
In filter 02...Ip...Src Port Cmp=None
In filter 02...Ip...Src Port #=N/A
In filter 02...Ip...Dst Port Cmp=Gtr
In filter 02...Ip...Dst Port #=1023
In filter 02..Ip..TCP Estab=No
In filter 03...Ip...Forward=Yes
In filter 03...Ip...Src Mask=0.0.0.0
In filter 03...Ip...Src Adrs=0.0.0.0
In filter 03...Ip...Dst Mask=0.0.0.0
In filter 03...Ip...Dst Adrs=0.0.0.0
In filter 03...Ip...Protocol=17
In filter 03...Ip...Src Port Cmp=None
In filter 03...Ip...Src Port #=N/A
In filter 03...Ip...Dst Port Cmp=Gtr
In filter 03...Ip...Dst Port #=1023
In filter 03.Ip...TCP Estab=No
In filter 04...Ip...Forward=Yes
In filter 04...Ip...Src Mask=0.0.0.0
In filter 04...Ip...Src Adrs=0.0.0.0
In filter 04...Ip...Dst Mask=0.0.0.0
In filter 04...Ip...Dst Adrs=0.0.0.0
In filter 04...Ip...Protocol=1
In filter 04...Ip...Src Port Cmp=None
In filter 04...Ip...Src Port #=N/A
In filter 04...Ip...Dst Port Cmp=None
In filter 04...Ip...Dst Port #=N/A
In filter 04.Ip...TCP Estab=No
Copyright © 1998, Ascend Communications, Inc. All rights reserved.