
![[Top]](../../images/home.jpg)
![[Contents]](../../images/contents.jpg)
![[Prev]](../../images/previous.jpg)
![[Next]](../../images/next.jpg)
![[Last]](../../images/index.jpg)


Setting Up User Authorization
User authorization enables you to tighten network security. You can control access on a per-user basis, and authorize access to selected enterprise resources and services. This chapter describes how to carry out the following user authorization tasks. This chapter contains:
Setting up terminal server security
A terminal server connection is host-to-host connection that uses analog modem, ISDN Terminal Adapter (using V.110 or V.120 encapsulation), or raw TCP. This section also applies to locally connected terminal server users, and describes how to limit access to the terminal server features such as Telnet server, raw-TCP, Rlogin server, and modem dialout. See Setting up authentication for dial-in terminal server users for more information about the authentication required before a remote user can get access to any of these features.
When the MAX receives an analog modem, ISDN TA, or raw TCP call, it determines whether the call is PPP-encapsulated. If it is, the MAX forwards the call to the router. If it is not PPP-encapsulated, the MAX establishes a terminal server connection.
In Figure 6-1, a PC running SoftComm initiates an incoming modem call. The MAX directs the call to its digital modems, and then forwards the call to its terminal server software. In Figure 6-1, the MAX immediately directs the call to a Telnet host.
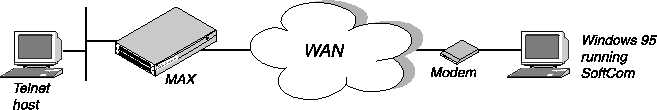
Figure 6-1. A remote terminal server connection
You can customize and limit access to the terminal server interface in these ways:
- Turn terminal server operation on or off.
- Specify customized prompts for remote terminal server users.
- Restrict use of terminal server commands and protocols.
- Restrict access to the terminal server command line.
- Restrict Telnet, raw TCP, and Rlogin access to the terminal server.
- Permit TCP-CLEAR or Telnet dial-in access even when the RADIUS user's profile does not specify a login host.
- Set a timeout value so that users are disconnected if they have not completed logging in when the timer has elapsed.
- Disconnect a user's Telnet connection using the session ID for the connection.
Table 6-1 lists the parameters you can use to customize and restrict access to the terminal server environment.
For complete information on setting up terminal server connections in the MAX configuration interface, see the MAX ISP & Telecommuting Configuration Guide. For complete information on setting up terminal server connections in RADIUS, see the RADIUS Configuration Guide .
Turning terminal server operation on or off
To specify whether users can access the terminal server interface, follow these steps:
- Open the Ethernet>Mod Config>TServ Options menu.
- To enable terminal server access, set TS Enabled=Yes; to disable terminal server access,
set TS Enabled=No.
- Save your changes.
Note: Any characters other than \n and \t that have a single backslash (\) in front of them
are removed.
For example, you could enter
Welcome to\n\t\\Ascend Remote Server\\\nEnter your user name:
to display the following on the terminal server screen:
Welcome to
\\Ascend Remote Server\\
Enter your user name:
Set Prompt Format=Yes.
This is the field that determines whether you are able to use the multi-line format for the terminal server prompt. If Prompt Format=No, the MAX does not interpret the line feed/carriage return character or the tab character.
Set the Login Timeout parameter.
This value can be an integer between 0 and 300 seconds. The default value is 300 seconds.
Users are disconnected if they have not completed logging in when the number of seconds set in the Login Timeout field has elapsed. A user has the total number of seconds indicated in the Login Timeout field to attempt a successful login. This means that the timer begins when the login prompt appears on the terminal server screen, and continues (is not reset) when the user makes unsuccessful login attempts.
To customize the password prompt, set the Password Prompt parameter.
This parameter specifies the prompt the terminal server displays when asking the user for his or her password. You can specify up to 80 characters. The default value is "Password:".
To specify a third prompt to follow the login and password prompts, specify a prompt
string in the 3rd Prompt parameter.
You can specify up to 20 characters. The default value is null. If you accept the default, the MAX does not display an additional prompt.
The remote terminal server user can enter up to 80 characters after this prompt. The MAX passes the information the user enters to the RADIUS server as an attribute called Ascend-Third-Prompt; this attribute appears in the Access-Request packet. If the user enters more than 80 characters, RADIUS truncates the data before assigning a value to the Ascend-Third-Prompt attribute.
The 3rd Prompt parameter does not apply if the Auth parameter has a value other than RADIUS or RADIUS/LOGOUT. If authentication occurs through a local Connection profile, and not through the RADIUS server, the MAX ignores the 3rd Prompt specification.
Select First or Last for the 3rd Prompt Seq parameter to select whether the additional
prompt appears at the beginning or the end of the login sequence.
3rd Prompt Seq works with any authentication method except Auth=None.
The default is Last. 3rd Prompt Seq is N/A if TS Enabled=No or 3rd Prompt= is empty.
The third prompt feature works slightly differently depending upon whether you specify that it appear in the Last position (a prompt issued after the login and password prompts) or the First position (a prompt issued before login and password prompts). For more complete information on how the third prompt feature works, see Understanding how the third login prompt works.
Save your changes.
Sample prompts
Suppose you accept the default settings for the Login Prompt and Password Prompt parameters, and specify this setting for 3rd Prompt:
3rd Prompt=Password2>>
The terminal server displays these prompts:
Login:
Password:
Password2>>
Understanding how the third login prompt works
You can configure a prompt by specifying the string that appears with the prompt and where it appears in the login sequence (first or last). This prompt can emulate an existing terminal server login prompt sequence, depending upon what you specify in the prompt string.
The third prompt feature works differently depending upon whether you select First or Last for the 3rd Prompt Seq parameter.
Similarities in the way the 3rd prompt works in either First or Last position are:
- Both work with any value for the Auth parameter except Auth=None.
- User's input is passed to RADIUS with the authentication request as the value of the Ascend-Third-Prompt RADIUS attribute.
Differences in the way the 3rd prompt works, depending upon whether 3rd Prompt Seq=First or Last, are:
- The First prompt appears before Login & Password prompts, the Last prompt appears after Login & Password prompt
- User's input is echoed in response to a First prompt and is not echoed in response to a Last prompt.
Restricting the use of terminal server commands and protocols
To specify whether users can initiate Telnet, Rlogin, PPP, or SLIP sessions from the terminal server interface, follow these steps:
- Open the Ethernet > Mod Config > TServ Options menu.
-
To specify whether a user can start a Telnet session, set the Telnet parameter.
- Yes indicates that a user can begin a Telnet session. The default value is Yes.
- No indicates that a user cannot begin a Telnet session.
- To specify whether a user can initiate an Rlogin session, set the Rlogin parameter.
- Yes indicates that a user can begin an Rlogin session.
- No indicates that a user cannot begin an Rlogin session. The default value is No.
- To specify whether a client can use asynchronous PPP, set the PPP parameter.
- Yes indicates that a client can use asynchronous PPP.
- No indicates that a client cannot use asynchronous PPP.
- The default value is No.
- To specify whether a user can initiate a SLIP (Serial Line IP) session, set the SLIP
parameter.
SLIP is a protocol that enables your computer to send and receive IP packets over a serial link.
- Yes indicates that a user can begin a SLIP session.
- No indicates that a user cannot begin a SLIP session. The default value is No.
- Save your changes.
Dial-in calls with no login host specified in RADIUS
You can configure the MAX to accept dial-in calls when Login-Service-TCP-CLEAR or Login-Service=Telnet, and no Login Host is specified in the RADIUS users file. This does not apply to PPP encapsulated calls, since the MAX does not accept dial-in PPP calls with the Login-Service set either to Telnet or TCP-CLEAR.
To set up the MAX to accept dial-calls when no login server is specified, set Auth TS Secure=No in the Ethernet > Mod Config > Auth menu. The default is Auth TS Secure=Yes, which means the MAX drops dial-in calls if there is no login server and Login-Server is Telnet or TCP-CLEAR.
Configuring per-user access to terminal server commands
The Framed Only parameter in the Answer profile and the Connection profiles enables you to limit specific users to the PPP, SLIP, CSLIP, and Quit commands in the MAX terminal server interface.You can configure per-user access to the terminal server commands in the Answer profile or in the Connection profile:
- The Answer profile affects users who do not have a Connection profile, users with a Name/Password profile, or RADIUS-authenticated users whose connections are built in part with the Answer profile
- The Connection profile only affects individual users connecting to the MAX using a particular Connection profile
To configure per-user access to the terminal server:
- Select Ethernet > Answer > Session Options or
Ethernet > Connections > a Connection profile > Session Options
- Specify one of the following values for Framed Only:
- Save and exit the profile.
If a user restricted to these commands tries to execute any other terminal server command, the MAX displays the following message:
Unauthorized Terminal Server Command.
Dealing with unauthorized Telnet and terminal server sessions
When a user activates a Security profile, the MAX generates a Syslog message notifying you that the event occurred. A user can activate a Security profile in a Telnet session or a serial-line COM port session by selecting the Security profile and specifying the proper password. When a user activates a Security profile, the new Syslog messages show the name of the Security profile, the IP address of the Telnet client or the COM port number, and the local IP address.
The EventSyslog message has one of these formats:
^DP(assword)ASCEND: "<profile_name>" ... for <remote_IP> on <local_IP>
ASCEND: "<profile_name>" ... from <COM_port> on <local_IP>
- The <profile_name> argument specifies the name of the activated Security profile.
- The <remote_IP> argument specifies the IP address of the Telnet client.
- The <local_IP> argument specifies the local IP address of the MAX.
- The <COM_port> argument specifies the COM port number for the session.
On system login, the MAX does not generate a Syslog message for the Default Security profile; for all events other than system login, the MAX generates a Syslog message for the Default Security profile. If Syslog is enabled, messages at LEVEL_NOTICE appear when a user activates a Security profile and the MAX accepts the Security profile password.
These two messages signal that a Telnet client has enabled a Security profile:
Jan 10 10:05:17 eng-lab-141 ASCEND: "Full Access" security profile
enabled for 206.65.212.9 on 192.168.6.141.
Jan 10 10:07:26 eng-lab-141 ASCEND: "Default" security profile enabled
for 206.65.212.23 on 192.168.6.141.
This message signals that a COM port user has enabled the Full Access profile:
Jan 10 10:03:52 eng-lab-141 ASCEND: "Full Access" security profile
enabled from com port 0 on 192.168.6.141.
Restricting access to the Immediate Modem feature
The Immediate Modem feature allows local terminal server users (who have not dialed into the MAX and have therefore not been authenticated) to Telnet to a MAX to access the MAX unit's modems, so that they can place outgoing calls without going through MAX terminal server interface. You can choose to restrict access to the Immediate Modem feature on a per-user basis, or you can specify a global password for all users. You can also disable call restriction for the Immediate Modem feature, so that all users can place outgoing calls.
To use immediate modem service, users specify the port number configured in the Imm. Modem Port parameter when opening a Telnet session to the MAX. For example, a user can access a digital modem on port 5000 in a MAX unit named "max1" by typing this command:
telnet> open max1 5000
When the modem responds, the user can begin entering AT commands to dial out.
Understanding per-user Immediate Modem access restriction
When per-user Immediate Modem is enabled, the MAX does the following:
- Requests a login name before allowing any user access to the Immediate Modem feature.
- The MAX attempts to find a profile with the name provided by the user, looking first for a
local Connection profile, then for a simple Name/Password profile, and finally for a
RADIUS profile.
- If the MAX finds a matching profile, it prompts the user for the password (if any) associated with the profile and verifies that the user enters the correct password.
- If no profile matching the name provided by the user can be found, the MAX rejects the user and closes the Telnet session.
- If the user enters the correct password, the MAX then checks the Dialout-OK parameter of
the appropriate profile.
- If Dialout OK is set to Yes, the user can access the immediate modem feature.
- If the user gets the password wrong or the Dialout OK parameter is set to No, the MAX rejects the user (with an appropriate message) and closes the telnet session.
Understanding password restriction for Immediate Modem
The immediate modem password separately governs whether a user is allowed to use the immediate modem functionality. If Telnet is password-protected, a user must know the Telnet password as well as the immediate modem password in order to dial out. To use Telnet but not the dialout functionality, a user only needs to know the Telnet password.
Configuring access to the Immediate Modem feature
To restrict access to the Immediate Modem feature, follow these steps:
- Open the Ethernet > Mod Config > TServ Options menu.
- Set TS Enabled=Yes.
The Imm. Modem Pwd field is N/A if TS Enabled=No. You cannot specify a password for the Immediate Modem feature.
- Set the Modem Dialout parameter to specify whether the user can use this MAX unit's
V.34 digital modems to dial out.
Modem Dialout=Yes permits terminal server users access the digital modems.
Modem Dialout=No denies terminal server users access to the digital modems. The defaul value is No.
- Set the Immediate Modem parameter to enable or disable the Immediate Modem feature.
Immediate Modem=Yes enables the Immediate Modem feature.
Immediate Modem=No disables the Immediate modem feature. The default value is Yes.
- Set the Imm. Modem Access parameter to specify whether the access is restricted on a
global or per-user basis, or unrestricted.
- None indicates that call restriction is disabled, and that all users can place outgoing calls.
- Global indicates that a single password exists for dialout (set in the Imm. Modem Pwd parameter). Any user who knows this password can place outgoing calls.
- User (the default) indicates the MAX requires a login before any user can access the Immediate Modem's dialout feature. The MAX attempts to match the user's name and password to a name and receive password in a Connection profile, Name/Password profile, or RADIUS users profile. If the user is authenticated by matching a Password profile, the Password profile must point to a Connection profile for the setting of the Dialout OK parameter.
- Specify a password in the Imm. Modem Pwd. parameter if you set Imm. Modem
Access=Global,
This parameter is N/A if Imm. Modem Access=None or User.
Note: To allow unlimited access to the Immediate Modem feature, set Imm. Modem
Access=None. Do not set Imm. Modem Access=Global and then leave the Imm. Modem
Pwd parameter null in order to allow unlimited access to the Immediate Modem feature.
- Close the Ethernet > Mod Config > TServ Options menu.
- Open the Telco options submenu of the appropriate Connection profile.
- Set the Dialout OK parameter to indicate whether modem dialout is allowed for this
Connection profile.
- Dialout OK=Yes indicates that the Connection profile allows modem dialout.
- Dialout OK=No indicates that the Connection profile does not allow modem dialout. Dialout OK=No is the default.
Disconnecting a user's terminal server session
You can disconnect a user who establishes a Telnet connection with the Ascend unit. You can disconnect the user by session ID. The disconnect code that results is identical to the RADIUS disconnect code, allowing you to track all administrative disconnects.
Displaying a list of active terminal server sessions
To display a list of active user session on an Ascend MAX, type:
show users
Note: at the terminal server prompt. show users displays a list of user sessions active on a
system. Each user session is identified by the sessionID, with additional information about the
session. The show users command has also been added to the online help for the show
command.
You can detect multiple concurrent sessions for the same user with the sessionActiveTable in the Ascend MIB.
Killing an active terminal server session
To terminate a Telnet session, enter this command line at the terminal server prompt:
kill <session ID>
For the <session ID> argument, specify the session ID as displayed by the terminal server "show users" command. The disconnect reason for the session is reported as DIS_LOCAL_ADMIN.
The active Security Profile must have Edit All Calls=Yes. If Edit All Calls=No, this message displays when you issue the kill command:
Insufficient security level for that operation.
If you issue the kill command without the <session ID> argument, this message displays:
kill command requires an argument
When the session is properly terminated, a message like this one displays:
Session 216747095 killed.
When the session is not terminated, a caution like this one displays:
Unable to kill session 216747095.
Setting up SNMP security
SNMP (Simple Network Management Protocol) provides a way for computers to share networking information. In SNMP, two types of communicating devices exist: agents and managers. An agent (such as the MAX) provides networking information to a manager application running on another computer. The agents and managers share a database of information, called the MIB (Management Information Base).
A trap is a mechanism in SNMP for reporting system change in real time. To report system change, the MAX sends a traps-PDU across the Ethernet interface to the SNMP manager. A complete list specifying the events that cause the MAX to send a traps-PDU appears in the Ascend Enterprise Traps MIB.
You can set up SNMP security in these ways:
- Specify passwords for SNMP managers with access to the MAX.
- Set up SNMP traps.
- Restrict the hosts that can issue SNMP commands.
Table 6-3 shows the parameters for protecting access to SNMP on the MAX.
Password-protecting SNMP
An SNMP manager application residing on a workstation on the local or remote network can access management information, set alarm thresholds, and change some settings on the MAX. To password protect this type of network access, you must assign the Read and Read/Write SNMP community strings. To assign Read and Read/Write SNMP community strings, follow these steps:
- Open the Ethernet>Mod Config>SNMP Options menu.
- Set the Read Comm parameter.
This parameter specifies the Read community string. This string authenticates an SNMP manager accessing the MAX to perform read commands-that is, the Get and Get Next commands. The Get command requests information. The Get Next command enables an SNMP manager to obtain a table of information, such as a routing table. After you enter a string for the Read Comm parameter, users must supply it to use the Get and Get Next commands.
- Set the R/W Comm parameter.
This parameter specifies the Read/Write community string. This string authenticates an SNMP manager accessing the MAX to perform read and write commands-that is, the Get, Get Next, and Set commands. The Set command enables an SNMP manager to change information maintained by the MAX. After you enter a string for the R/W Comm parameter, users must supply it to use the Get, Get Next, and Set commands. You can use the original SNMPv1 definition of the community string (a string of octets that is compared to a similar string in the receiving SNMP entity). If the string in the packet received exactly matches a community string in the receiving entity, then the packet is considered "authentic".
The defaults for SNMP v1 (without authentication) are:
Ethernet > Mod Config > SNMP Options > Read Comm=public
Ethernet > Mod Config > SNMP Options > R/W Comm=write
You use a new version of the Read/Write community string if you wish to use SNMP authentication, with the format:
Ethernet > Mod_config > SNMP Options > R/W Comm=write|secretkey
This causes the Ascend unit to require SNMP SET REQUEST packets to be authenticated, using "secretkey" as the shared (but not transmitted) secret.
- name is the name you want to assign to the read-write community name.
- secretkey is the alphanumeric key used for authentication.
- a vertical bar separates the name from the secretkey.
The data, time, and hash values are transmitted with the packet. This allows the management station and Ascend unit to verify that the packet has been produced by an authorized system, and that the packet not been altered or significantly delayed in transmission.
The MD5 hash guarantees a high likelihood that only a system that knows the secret authentication key generated the packet, while the time variables guarantee a high likelihood that an attacker did not collect an authenticated packet and transmit it at a time of its own choosing, after a significant delay.
Note: You cannot turn SNMP write off, so you must set a secret R/W Comm string. The
default R/W Comm string is "write". Anyone who has used an Ascend product probably
knows this default string, so it does not provide any real security.
- If you are using authenticated SNMP, configure the SNMP management station to
communicate with a MAX using authenticated SNMP. See "Configuring the SNMP
manager to use SNMP authentication."
- Save your changes.
Configuring the SNMP manager to use SNMP authentication
To communicate with an Ascend unit that has been configured to use authenticated SNMP, an SNMP management station must construct an SNMP packet using the new format for the Read/Write community string, including the secret key:
name|secretkey
If the Ascend unit has been configured to use authenticated SNMP, it will not accept packets from an SNMP management station using the string format without the pipe/vertical bar.
Setting up SNMP traps
To configure parameters related to SNMP traps security, follow these steps:
- Open the Ethernet>SNMP Traps menu.
- Open a blank SNMP Traps profile.
- For the Name parameter, specify the SNMP manager to which the MAX sends traps-
PDUs.
You can specify up to 31 characters. The default value is null. The value you specify becomes the name of the profile.
- Set the Alarm parameter.
This parameter specifies whether the MAX sends a traps-PDU to the SNMP manager when an alarm event occurs. Alarm events are defined in RFC 1215 and include the following:
- coldStart. This event indicates that the MAX started up from a power-off condition.
- warmStart. This event indicates that the MAX started up from a power-on condition, typically by a system reset.
- linkDown. This event indicates that a WAN link or Ethernet interface has gone offline.
- linkUp. This event indicates that a WAN link or Ethernet interface has come online.
You can specify either Yes or No for the Alarm parameter. Yes specifies that the MAX traps alarm events. No specifies that the MAX does not trap alarm events. The default value is Yes.
- Set the Port parameter.
This parameter specifies whether the MAX traps serial host port state changes and sends traps-PDUs to the SNMP manager. The MAX can record these serial host port events:
- portInactive
- portDualDelay
- portWaitSerial
- portHaveSerial
- portRinging
- portCollectDigits
- portWaiting
- portConnected
- portCarrier
- portLoopback
- portAcrPending
- portDteNotReady
You can specify either Yes or No for the Port parameter. Yes specifies that the MAX traps serial host port state changes. No specifies that the MAX ignores serial host port state changes. The default value is No.
- Set the Security parameter.
This parameter specifies whether the MAX traps these events:
- authenticationFailure. This event occurs when authentication has failed. See RFC-1215 for a full explanation of this event.
- consoleStateChange. This event occurs when a VT100, Palmtop, or Telnet port changes its state.
- portUseExceeded. This event occurs when the port exceeds the maximum number of DS0 minutes set by the Max DS0 Mins parameter in the Port profile.
- systemUseExceeded. This event occurs when the MAX exceeds the maximum number of DS0 minutes set by the Max DS0 Mins parameter in the System profile.
You can specify either Yes or No for the Security parameter. Yes specifies that the MAX traps the events. No specifies that the MAX does not trap the events. The default value is No.
- Using the Comm parameter, specify a community name.
The string you specify becomes a password that the MAX sends to the SNMP manager when an SNMP trap event occurs. The password authenticates the sender identified by the IP address in the IP Adrs parameter.
For the community name, you can enter an alphanumeric string containing up to 31 characters. The default value is null. To turn off SNMP traps, leave the Comm parameter blank and set Dest=0.0.0.0.
- Using the Dest parameter, specify the IP address of the SNMP manager to which the
MAX sends traps-PDUs.
Specify an IP address in dotted decimal notation. An IP address consists of four numbers between 0 and 255, separated by periods. If a netmask is in use, you must specify it. Separate a netmask from the IP address with a slash. The default value is 0.0.0.0/0.
The MAX ignores any digits in the IP address hidden by a netmask. For example, the address 200.207.23.1/24 becomes 200.207.23.0. To specify a route to a specific host, use a mask of 32.
The Dest parameter does not apply if the MAX does not support IP (Route IP=No) or if Combinet encapsulation is in use (Encaps=COMB).
- Save your changes.
Restricting the hosts that can issue SNMP commands
The MAX is an SNMP-enabled device that supports a variety of MIBs. Especially on a large network, you may want to specify which stations can use SNMP manager applications to initiate read or read/write access to those MIBs.
You can specify up to five IP hosts that can read traps and other information from the Ascend unit, and five hosts that can access MIB read-write access. The MAX checks the version and community strings before making source IP address comparisons.
To restrict the hosts that can issue SNMP commands, follow these steps:
- Open the Ethernet>Mod Config>SNMP Options menu.
- Make sure that the Security parameter is set to Yes.
This parameter specifies that the MAX must compare the source IP address of packets containing SNMP commands against a list of qualified IP addresses.
- Specify the IP addresses of hosts that have SNMP read permission.
For example, you might make these settings:
RD Mgr1=10.1.2.3
RD Mgr2=10.1.2.4
RD Mgr3=10.1.2.5
RD Mgr4=10.1.2.6
RD Mgr5=10.1.2.7
If the Security parameter is set to Yes, only SNMP managers at the specified IP addresses can execute the SNMP Get and Get Next commands.
- Specify the IP addresses of hosts that have SNMP write permission.
For example, you might make these settings:
WR Mgr1=10.9.8.1
WR Mgr2=10.9.8.2
WR Mgr3=10.9.8.3
WR Mgr4=10.9.8.4
WR Mgr5=10.9.8.5
If the Security parameter is set to Yes, only SNMP managers at the specified IP addresses can execute the SNMP Get, Get Next, and Set commands.
- Save your changes.
Setting up DNS (Domain Name System)
DNS is a TCP/IP service that enables you to specify a symbolic name instead of an IP address. A symbolic name consists of a username and a domain name using the format <username>@<domain name>. The username corresponds to the host number in the IP address; the domain name corresponds to the network number in the IP address. A symbolic name might be steve@abc.com or joanne@xyz.edu.
DNS maintains a database of network numbers and corresponding domain names on a domain name server. When you use a symbolic name, DNS translates the domain name into an IP address, and sends it over the network. When the Internet service provider receives the message, it uses its own database to look up the username corresponding to the host number.
You can set up two types of DNS configurations:
Table 6-4 lists the parameters you can set.
Setting global DNS parameters
To set global DNS parameters, follow these steps:
- Open the Ethernet>Mod Config>DNS menu.
- To specify a primary domain name to use for lookups, set the Domain Name parameter.
The MAX searches for the DNS Server(s) in the Domain Name parameter first, and then in the domain specified in the Sec Domain Name parameter.
- To specify a secondary domain name to use for lookups, set the Sec Domain Name
parameter.
The MAX searches for the DNS Server(s) first in the domain specified by the Domain Name parameter, and then in the domain specified in the Sec. Domain Name parameter.
- Using the Pri DNS parameter, specify the IP address of the primary domain name server
for use on connected local interfaces.
The address consists of four numbers between 0 and 255, separated by periods. The default value is 0.0.0.0. Accept this default if you do not have a domain name server.
- Using the Sec DNS parameter, specify the IP address of the secondary domain name
server for use on connected local interfaces.
The address consists of four numbers between 0 and 255, separated by periods. The default value is 0.0.0.0. Accept this default if you do not have a secondary domain name server.
The MAX uses the secondary server only if the primary one is inaccessible. The Sec DNS parameter applies only to Telnet and raw TCP connections running under the MAX unit's terminal server interface.
- Set List Attempt=Yes.
DNS can return multiple addresses for a hostname in response to a DNS query, but it does not include information about availability of those hosts. Users typically attempt to access the first address in the list. If that host is unavailable, the user must try the next host, and so forth. However, if the access attempt occurs automatically as part of immediate services, the physical connection is torn down when the initial connection fails.
The DNS List Attempt feature helps the MAX avoid tearing down physical links by enabling the user to try one entry in the DNS list of hosts when logging in through Telnet from the terminal server or immediate Telnet; if that connection fails, the user can try each succeeding entry.
You can specify one of these settings:
- Yes specifies that the MAX enables a user to try the next host in the DNS list if the first Telnet login attempt fails.
- No turns off the List Attempt feature.
- The default value is No.
- If you set List Attempt=Yes, set the List Size parameter.
- The List Size parameter specifies the maximum number of hosts the MAX can list in
response to a DNS query. You can specify a number between 0 and 35. The default value
is 6. Set the Client Pri DNS parameter.
- MAXhe Client Sec DNS parameter.
MAXMAXThe default value is 0.0.0.0. Accept this default if you do not have a secondary client DNS server.
- Set the Allow As Client DNS parameter.
- Yes enables WAN clients to use local DNS servers.
- No disables WAN clients from using local DNS servers.
- No is the default.
Sample DNS configuration
This sample specifies two local DNS servers and enables the DNS list feature.
- Open the Ethernet>Mod Config>DNS menu.
- Specify your domain name.
- Specify the IP addresses of a primary and secondary DNS server, and turn on the DNS list
attempt feature.
Mod Config
DNS
Domain Name=abc.com
Pri DNS=10.2.3.56/24
Sec DNS=10.2.3.107/24
List Attempt=Yes
- Save your changes.
Setting connection-specific DNS parameters
To set up connection-specific DNS parameters, follow these steps:
- Open the Ethernet>Connections menu.
- Open a Connection profile
- Open the IP Options menu.
- Set the Client Pri DNS parameter.
- MAXSet the Client Sec DNS parameter.
Disabling remote management access
To prevent an operator from accessing the MAX from a remote Ascend unit using AIM or MP+ remote management, set System > Sys Config > Remote Mgmt = No
To disable remote management access, follow these steps:
- Open the System>Sys Config menu.
- Set Remote Mgmt=No.
- Exit and save your changes.
For related information on remote management, see the chapter on system administration in the MAX ISP and Telecommuting Configuration Guide.
Password-protecting Telnet access
You can restrict operators from accessing the MAX across the network from a remote PC running Telnet by setting Ethernet > Mod Config > Telnet PW.
To assign a Telnet password, follow these steps:
- Open the Ethernet>Mod Config menu.
- Set the Telnet PW parameter.
The Telnet password you supply can contain up to 20 characters. Any user who initiates an incoming Telnet session to the MAX must supply this password before the Telnet session is established.
If a user initiates the Telnet session from the WAN, the connection must first be authenticated as specified in a Connection profile.
See Restricting Telnet, raw TCP, and Rlogin access to the terminal server for additional information about restricting Telnet in the terminal server interface.
- Save your changes.
Note: The Telnet password does not automatically grant access to the Immediate Modem
feature, which allows a user to dial out through the MAX modems without going through the
terminal server interface. See Restricting access to the Immediate Modem feature for more
information.
DBA (Dynamic Bandwidth Allocation) enables the MAX to increase bandwidth as needed and drop bandwidth when it is no longer required. MP+ is the only PPP-based encapsulation method that supports DBA.
When the system adds additional channels, the MAX must authenticate each one. You can secure each circuit using one of the following methods:
- Static passwords
Before the MAX dials a new circuit, it prompts the user to enter a static, reusable password as specified in the Connection profile, Password profile, RADIUS user profile, or TACACS/TACACS+ profile. To prevent intruders from capturing the password as it travels across the WAN, you can specify that the MAX use the Challenge Handshake Authentication Protocol (CHAP). This protocol uses encryption to protect the password and verify the identity of the caller.
For information on specifying a static password and requiring CHAP authentication in the MAX configuration interface, see Configuring PAP, CHAP, or MS-CHAP for PPP, MP, and MP+ calls. For information on configuring static passwords and CHAP in RADIUS, see the MAX RADIUS Configuration Guide.
- Dynamic passwords
Using PAP-TOKEN authentication, the MAX can require a user to specify a one-time-only password, generated by a security-card server, for each additional channel.
For information on setting up PAP-TOKEN authentication in the MAX configuration interface, see Requesting PAP-TOKEN authentication. For information on setting up PAP-TOKEN authentication in RADIUS, see the MAX RADIUS Configuration Guide.
- Combination of static and dynamic password
In the MAX configuration interface, you can indicate that the user need only specify a dynamic password for the initial channel, and that all other channels are authenticated by CHAP. Whenever the MAX adds channels to a PPP or MP+ call using PAP-TOKEN-CHAP authentication, the calling unit sends the encrypted value of Aux Send PW (found in the Connection profile used to dial the call), and the answering unit checks this password against the value of Recv Auth (in a Connection profile) or Ascend-Receive-Secret (in a RADIUS user profile). The answering unit receives the password when the first channel of the call connects.
For details on setting up PAP-TOKEN-CHAP authentication in the MAX configuration interface, see Requesting PAP-TOKEN-CHAP authentication. For information on setting up PAP-TOKEN-CHAP authentication in RADIUS, see the MAX RADIUS Configuration Guide.
- Cached passwords
You can configure the MAX to reuse a password dynamically generated during session initiation. In this case, both the user and the MAX cache the password. Then, when the MAX needs to add bandwidth, the user provides the CHAP-encrypted password automatically and the MAX uses an internal key to authenticate the additional channels. You can specify a timeout value for the cached password, or configure the MAX to maintain the password throughout the session.
For details on setting up cached passwords in the MAX configuration interface, see Requesting CACHE-TOKEN authentication. For information on setting up cached passwords in RADIUS, see the MAX RADIUS Configuration Guide.
![[Top]](../../images/home.jpg)
![[Contents]](../../images/contents.jpg)
![[Prev]](../../images/previous.jpg)
![[Next]](../../images/next.jpg)
![[Last]](../../images/index.jpg)


techpubs@eng.ascend.com
Copyright © 1998, Ascend Communications, Inc. All rights
reserved.

