
![[Top]](../../images/home.jpg)
![[Contents]](../../images/contents.jpg)
![[Prev]](../../images/previous.jpg)
![[Next]](../../images/next.jpg)
![[Last]](../../images/index.jpg)


Setting Up Virtual Private Networks
This chapter covers these topics:
Introduction to virtual private networks
Virtual Private Networks provide low-cost remote access to private LANs via the Internet. The tunnel to the private corporate network can be from an ISP, enabling mobile nodes to dial-in to a corporate network, or it can provide a low-cost Internet connection between two corporate networks. Ascend currently supports these VPN schemes: Ascend Tunnel Management Protocol (ATMP), Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP).
An ATMP session occurs between two Ascend units via UDP/IP. The MAX encapsulates all packets passing through the tunnel in standard GRE (Generic Routing Encapsulation) as described in RFC 1701. ATMP creates and tears down a cross-Internet tunnel between the two Ascend units. In effect, the tunnel collapses the Internet cloud and provides what looks like direct access to a home network. The tunnels do not support bridging. All packets must be routed with IP or IPX.
Point-to-Point-Tunneling Protocol (PPTP) was developed by Microsoft Corporation to enable Windows 95 and Windows NT Workstation users to dial into a local ISP to connect to a private corporate network across the Internet.
Layer 2 Tunneling Protocol (L2TP) is specified in version 8 of the Internet Engineering Task Force (IETF) draft titled Layer Two Tunneling Protocol "L2TP," dated November, 1997. L2TP enables you to connect to a private network by dialing into a local MAX, which creates and maintains an L2TP tunnel between itself and the private network.
The MAX does not support dial-in users, so its support of PPTP consists of routing or forwarding PPTP traffic as appropriate. The MAX does not act as either a PPTP Access Concentrator (PAC) or a PPTP Network Server (PNS).
Configuring ATMP tunnels
This section describes how ATMP tunnels work between two MAX units. One of the units acts as a foreign agent (typically a local ISP) and one as a home agent (which can access the home network). A mobile node dials into the foreign agent, which establishes a cross-Internet IP connection to the home agent. The foreign agent then requests an ATMP tunnel on top of the IP connection. The foreign agent must use RADIUS to authenticate mobile nodes dial-ins.
The terminating part of the tunnel is the home agent, where most of the ATMP intelligence takes place. It must be able to communicate with the home network (the destination network for mobile nodes) through a direct connection, another router, or across a nailed connection.
For example, in Figure 13-1, the mobile node might be a sales person who logs into an ISP to access his or her home network. The ISP is the foreign agent. The home agent has access to the home network.
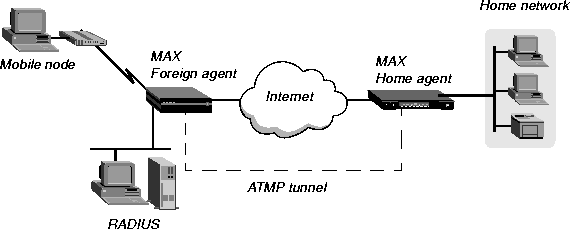
Figure 13-1. ATMP tunnel across the Internet
How the MAX creates ATMP tunnels
This is how the MAX establishes an ATMP tunnel connection:
- A mobile node dials a connection to the foreign agent.
- The foreign agent authenticates the mobile node using a RADIUS profile.
The MAX requires RADIUS authentication of the mobile node, because RADIUS only supports the required attributes.
- The foreign agent uses the Ascend-Home-Agent-IP-Addr attribute in the mobile node's
RADIUS profile to locate a Connection profile (or RADIUS profile) for the home agent.
- The foreign agent dials the home agent, and authenticates and establishes an IP connection
in the usual way.
- The foreign agent informs the home agent that the mobile node is connected, and requests
a tunnel. It sends up to 10 RegisterRequest messages at 2-second intervals, timing out and
logging a message if it receives no response to those requests.
- The home agent requests a password before it creates the tunnel.
- The foreign agent returns an encrypted version of the Ascend-Home-Agent-Password
found in the mobile node's RADIUS profile. This password must match the home agent's
Password parameter in the ATMP configuration in the Ethernet Profile.
- The home agent returns a RegisterReply with a number that identifies the tunnel. If
registration fails, the MAX logs a message and the foreign agent disconnects the mobile
node. If registration succeeds, the MAX creates the tunnel between the foreign agent and
the home agent.
- When the mobile node disconnects from the foreign agent, the foreign agent sends a
DeregisterRequest to the home agent to close down the tunnel.
The foreign agent can send its request a maximum of ten times, or until it receives a DeregisterReply. If the foreign agent receives packets for a mobile node whose connection has been terminated, the foreign agent silently discards the packets.
Router and gateway mode
The home agent can communicate with the home network through a direct connection, through another router, or across a nailed connection. When the home agent relies on packet routing to reach the home network, it operates in router mode. When it has a nailed connection to the home network, it is in gateway mode.
Configuring the foreign agent
The parameters related to foreign agent configuration are:
Ethernet
Mod Config
ATMP options...
ATMP Mode=Foreign
Type=N/A
Password=N/A
SAP Reply=N/A
UDP Port=5150
For the IP routing connection to the home agent:
Ethernet
Mod Config
Ether options...
IP Adrs=10.65.212.226/24
Ethernet
Connections
Station=home-agent
Active=Yes
Dial #=555-1212
Route IP=Yes
IP options...
LAN Adrs=10.1.2.3/24
To use RADIUS for authentication:
Ethernet
Mod Config
Auth...
Auth=RADIUS
Auth Host #1=10.23.45.11/24
Auth Host #2=0.0.0.0/0
Auth Host #3=0.0.0.0/0
Auth Port=1645
Auth Timeout=1
Auth Key-=[]
Auth Pool=No
Auth Req=Yes
Password Server=No
Password Port=N/A
Local Profile First=No
Sess Timer=0
Auth Src Port=0
Auth Send Attr 6,7=Yes
RADIUS user profiles for mobile nodes running TCP/IP:
node1 Password="top-secret"
Ascend-Metric=2,
Framed-Protocol=PPP,
Ascend-IP-Route=Route-IP-Yes,
Framed-Address=200.1.1.2,
Framed-Netmask=255.255.255.0,
Ascend-Primary-Home-Agent=10.1.2.3,
Ascend-Home-Agent-Password="private"
Ascend-Home-Agent-UDP-Port = 5150
RADIUS user profiles for mobile nodes running NetWare:
node2 Password="ipx-unit"
User-Service=Framed-User,
Ascend-Route-IPX=Route-IPX-Yes,
Framed-Protocol=PPP,
Ascend-IPX-Peer-Mode=IPX-Peer-Dialin,
Framed-IPX-Network=40000000,
Ascend-IPX-Node-Addr=123456789012,
Ascend-Primary-Home-Agent=10.1.2.3,
Ascend-Home-Agent-Password="private"
For more information on each parameter, see the MAX Reference Guide. For details on attributes and configuring external authentication, see the MAX RADIUS Configuration Guide.
Understanding the foreign agent parameters and attributes
This section provides some background information on configuring a foreign agent to initiate an ATMP request to the home agent MAX.
Foreign agent parameters
|
Description
|
|---|
|
ATMP mode
|
For the foreign agent, the mode is Foreign, which makes the type, password, and SAP Reply fields not applicable.
|
|
UDP port
|
ATMP uses UDP port 5150 for ATMP messages between the foreign and home agents. If you specify a different UDP port number, make sure that the entire ATMP configuration agrees.
|
|
IP configuration and Connection profile
|
The cross-Internet connection to the home agent is an IP routing connection, which the MAX authenticates and establishes in the usual way. For details, see Chapter 10, Configuring IP Routing.
|
|
Configuring the foreign agent to authenticate using RADIUS
|
The foreign agent must use RADIUS to authenticate mobile nodes, and the RADIUS server must be running a version of the daemon that includes the ATMP attributes. For details, see the MAX RADIUS Configuration Guide.
|
|
Creating a RADIUS user profile for a mobile node running TCP/IP
|
The RADIUS user profiles for mobile nodes must set ATMP attributes. The required attributes differ slightly depending on whether the mobile node and home network run IP or IPX and whether the home agent MAX operates in router mode or gateway mode.
|
The required attributes when the mobile node and home network are routing IP are:
The required attributes when the mobile node and home network are routing IPX are:
The foreign agent attributes and their descriptions are:
Example foreign agent configuration (IP)
To configure the foreign agent and create a mobile node profile to access a home IP network:
- Open Ethernet > Mod Config > Ether Options and verify that the LAN interface has an IP
address. For example:
Ethernet
Mod Config
Ether options...
IP Adrs=10.65.212.226/24
- Open the ATMP Options subprofile and set ATMP Mode to Foreign.
ATMP options...
ATMP Mode=Foreign
Type=N/A
Password=N/A
SAP Reply=N/A
UDP Port=5150
- Open the Auth subprofile and configure the foreign agent to authenticate using RADIUS.
For example:
Auth...
Auth=RADIUS
Auth Host #1=10.23.45.11/24
Auth Host #2=0.0.0.0/0
Auth Host #3=0.0.0.0/0
Auth Port=1645
Auth Timeout=1
Auth Key-=[]
Auth Pool=No
Auth Req=Yes
Password Server=No
Password Port=N/A
Local Profile First=No
Sess Timer=0
Auth Src Port=0
Auth Send Attr 6,7=Yes
For details, see the MAX RADIUS Configuration Guide.
- Close the Ethernet profile.
- Open a Connection profile and configure an IP routing connection to the home agent. For
example:
Ethernet
Connections
Station=home-agent
Active=Yes
Encaps=MPP
Dial #=555-1212
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=home-pw
Send PW=foreign-pw
IP options...
LAN Adrs=10.1.2.3/24
- Close the Connection profile.
- On the RADIUS server, open the RADIUS user profile and create an entry for a mobile
node. For example:
node1 Password="top-secret"
Ascend-Metric=2,
Framed-Protocol=PPP,
Ascend-IP-Route=Route-IP-Yes,
Framed-Address=200.1.1.2,
Framed-Netmask=255.255.255.0,
Ascend-Primary-Home-Agent=10.1.2.3,
Ascend-Home-Agent-Password="private"
Ascend-Home-Agent-UDP-Port = 5150
- Close the user profile.
When the mobile node logs into the foreign agent with the password "top-secret", the foreign agent authenticates the mobile node using RADIUS. It then looks for a profile with an IP address that matches the Ascend-Home-Agent-IP-Addr value, so it can bring up an IP connection to the home agent.
Example foreign agent configuration (IPX)
The foreign agent configuration to support IPX connections via ATMP is the same as the one shown in the previous section. The only difference is in the mobile node's user profile. For example:
node2 Password="ipx-unit"
User-Service=Framed-User,
Ascend-Route-IPX=Route-IPX-Yes,
Framed-Protocol=PPP,
Ascend-IPX-Peer-Mode=IPX-Peer-Dialin,
Framed-IPX-Network=40000000,
Ascend-IPX-Node-Addr=123456789012,
Ascend-Primary-Home-Agent=10.1.2.3,
Ascend-Home-Agent-Password="private"
When the mobile node logs into the foreign agent with the password ipx-unit, the foreign agent authenticates the mobile node using RADIUS. It then looks for a profile with an IP address that matches the Ascend-Home-Agent-IP-Addr value, so it can bring up an IP connection to the home agent.
Configuring a home agent in router mode
When the ATMP tunnel has been established between the home agent and foreign agent, the home agent in router mode receives IP packets through the tunnel, removes the GRE encapsulation, and passes the packets to its bridge/router software. It also adds a host route to the mobile node to its routing table.
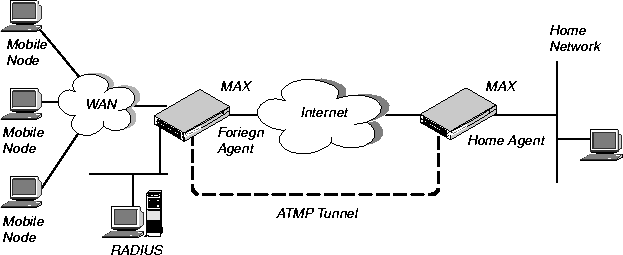
Figure 13-2. Home agent routing to the home network
The MAX requires the IPX routing parameters in the Ethernet profile only if the MAX is routing IPX. These are the parameters for configuring a home agent in router mode:
Ethernet
Mod Config
IPX Routing=Yes
Ether options
IP Adrs=10.1.2.3/24
IPX Frame=802.2
IPX Enet #=00000000
ATMP options...
ATMP Mode=Home
Type=Router
Password=private
SAP Reply=No
UDP Port=5150
For the IP routing connection to the foreign agent:
Ethernet
Connections
Station=foreign-agent
Active=Yes
Encaps=MPP
Dial #=555-1213
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=foreign-pw
Send PW=home-pw
IP options...
LAN Adrs=10.65.212.226/24
Understanding the ATMP router mode parameters
This section provides some background information on configuring a home agent in router mode. For more information on each parameter, see the MAX Reference Guide.
ATMP mode and type
For the home agent, the mode is Home. When you set the ATMP Type to Router, the home agent relies on routing (not a WAN connection) to pass packets received through the tunnel to the home network.
Password
This is the password used to authenticate the ATMP tunnel itself, which must match the password specified in the Ascend-Home-Agent-Password attribute of mobile nodes' RADIUS profiles. (All mobile nodes use the same password for that attribute.)
SAP Reply
This enables a home agent to reply to the mobile node's IPX Nearest Server Query if it knows about a server on the home network. If set to No, the home agent simply tunnels the mobile node's request to the home network.
UDP port
ATMP uses UDP port 5150 for ATMP messages between the foreign and home agents. If you specify a different UDP port number, make sure that the entire ATMP configuration agrees.
IP configuration and Connection profile
The cross-Internet connection to the foreign agent is an IP routing connection, which the MAX authenticates and establishes in the usual way. For details, see Chapter 10, Configuring IP Routing.
Notes about routing to the mobile node
When the home agent receives IP packets through the ATMP tunnel, it adds a host route for the mobile node to its IP routing table. It then handles routing in the usual way. When the home agent receives IPX packets through the tunnel, it adds a route to the mobile node based on the virtual IPX network number assigned in the RADIUS user profile.
For IP routes, you can enable RIP on the home agent's Ethernet to enable other hosts and networks to route to the mobile node. Enabling RIP is particularly useful if the home network is one or more hops away from the home agent's Ethernet. If you turn RIP off, other routers require static routes that specify the home agent as the route to the mobile node.
Note: If the home agent's Ethernet is the home network (a direct connection), you should turn
on proxy ARP in the home agent to enable local hosts to ARP for the mobile node.
For details on IP routes, see Configuring IP Routing. For information about IPX routes, see Configuring IPX Routing.
Example home agent in router mode (IP)
To configure the home agent in router mode to reach an IP home network:
- Open Ethernet > Mod Config > Ether Options and verify that the LAN interface has an IP
address. You may also set routing options, for example:
Ethernet
Mod Config
Ether options...
IP Adrs=10.1.2.3/24
RIP=On
- Open the ATMP Options subprofile, set ATMP Mode to Home, and ATMP Type to
Router.
- Specify the password used to authenticate the tunnel (Ascend-Home-Agent-Password).
ATMP options...
ATMP Mode=Home
Type=Router
Password=private
SAP Reply=No
UDP Port=5150
- Close the Ethernet profile.
- Open a Connection profile and configure an IP routing connection to the foreign agent.
For example:
Ethernet
Connections
Station=foreign-agent
Active=Yes
Encaps=MPP
Dial #=555-1213
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=foreign-pw
Send PW=home-pw
IP options...
LAN Adrs=10.65.212.226/24
- Close the Connection profile.
Example home agent in router mode (IPX)
To configure the home agent in router mode to reach an IPX network:
- Open Ethernet > Mod Config > Ether Options and verify that the LAN interface has an IP
address (needed to communicate with the foreign agent) and can route IPX.
Ethernet
Mod Config
IPX Routing=Yes
Ether options
IP Adrs=10.1.2.3/24
IPX Frame=802.2
IPX Enet #=00000000
For details, see Chapter 9, Configuring IPX Routing.
- Open the ATMP Options subprofile and set ATMP Mode to Home and Type to Router.
- Specify the password used to authenticate the tunnel (Ascend-Home-Agent-Password).
- Set SAP Reply to Yes.
ATMP options...
ATMP Mode=Home
Type=Gateway
Password=private
SAP Reply=Yes
UDP Port=5150
- Close the Ethernet profile.
- Open a Connection profile and configure an IP routing connection to the foreign agent.
For example:
Ethernet
Connections
Station=foreign-agent
Active=Yes
Encaps=MPP
Dial #=555-1213
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=foreign-pw
Send PW=home-pw
IP options...
LAN Adrs=10.65.212.226/24
- Close the Connection profile.
Configuring a home agent in gateway mode
When you configure the home agent configured in gateway mode, it receives GRE-encapsulated IP packets from the foreign agent, strips off the encapsulation, and passes the packets across a nailed WAN connection to the home network.
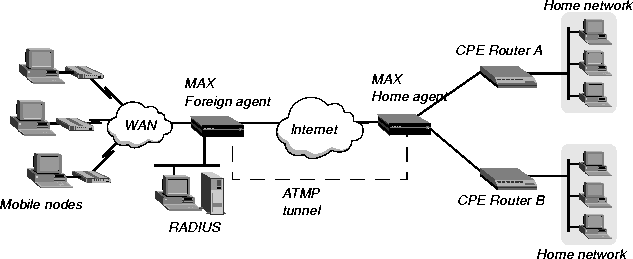
Figure 13-3. Home agent in gateway mode
Note: To enable hosts and routers on the home network to reach the mobile node, you must
configure a static route in the CPE (customer premise equipment) router on the home network
(not in the home agent). The static route must specify the home agent as the route to the mobile
node; that is, the route's destination address specifies the Framed-Address of the mobile node,
and its gateway address specifies the IP address of the home agent.
These are the parameters for configuring a home agent in gateway mode:
Ethernet
Mod Config
IPX Routing=Yes
Ether options
IP Adrs=10.1.2.3/24
IPX Frame=802.2
IPX Enet #=00000000
ATMP options...
ATMP Mode=Home
Type=Gateway
Password=private
SAP Reply=No
UDP Port=5150
For the IP routing connection to the foreign agent:
Ethernet
Connections
Station=foreign-agent
Active=Yes
Encaps=MPP
Dial #=555-1213
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=foreign-pw
Send PW=home-pw
IP options...
LAN Adrs=10.65.212.226/24
For the nailed connection to the home network:
Ethernet
Connections
Station=homenet
Active=Yes
Encaps=MPP
Dial #=N/A
Calling #=N/A
Route IP=Yes
Route IPX=Yes
IP options...
LAN Adrs=5.9.8.2/24
Telco options...
Call Type=Nailed
Group=1,2
Session options...
ATMP Gateway=Yes
MAX ATMP Tunnels=0
The IPX routing parameters are required only if the MAX is routing IPX. For more information on each parameter, see the MAX Reference Guide.
Understanding the ATMP gateway mode parameters
This section provides some background information on configuring a home agent in gateway mode.
ATMP mode and type
For the home agent, the mode is Home. When you set the ATMP Type to Gateway, the home agent forwards packets received through the tunnel to the home network across a nailed WAN connection.
Password
This is the password used to authenticate the ATMP tunnel itself, which must match the password specified in the Ascend-Home-Agent-Password attribute of mobile nodes' RADIUS profiles. (All mobile nodes use the same password for that attribute.)
SAP Reply
This enables a home agent to reply to the mobile node's IPX Nearest Server Query if it knows about a server on the home network. If set to No, the home agent simply tunnels the mobile node's request to the home network.
UDP port
ATMP uses UDP port 5150 for ATMP messages between the foreign and home agents. If you specify a different UDP port number, make sure that the entire ATMP configuration agrees.
IP configuration and Connection profile
The cross-Internet connection to the foreign agent is an IP routing connection, which the MAX authenticates and establishes in the usual way. For details, see Chapter 10, Configuring IP Routing.
Connection profile to the home network
The Connection profile to the home network must be a local profile, it cannot be specified in RADIUS. The name of this Connection profile must match the name in the Ascend-Home-Network-Name attribute in the mobile node's RADIUS profile. In addition, the Connection profile to the home network must specify these values:
- Nailed call type. The home agent must have a nailed connection to the home network, because it does dial the WAN connection based on packets received through the tunnel.
- ATMP Gateway session option. The ATMP Gateway parameter must be set to Yes. This parameter instructs the home agent to send data it receives back from the home network on this connection to the mobile node.
- MAX ATMP Tunnels session option. The MAX ATMP Tunnels parameter allows an administrator of the MAX to limit the number of ATMP tunnels that can be established from a home agent gateway to a home network. The MAX acts as the home agent gateway. On a home agent, the maximum number of ATMP tunnels can be specified individually for each home network.
Example home agent in gateway mode (IP)
To configure the home agent in gateway mode to reach an IP home network:
- Open Ethernet > Mod Config > Ether Options and verify that the LAN interface has an IP
address. For example:
Ethernet
Mod Config
Ether options...
IP Adrs=10.1.2.3/24
- Open the ATMP Options subprofile and set ATMP Mode to Home and Type to Gateway.
- Specify the password used to authenticate the tunnel. This must match the
Ascend-Home-Agent-Password attribute of mobile nodes' RADIUS profiles.
ATMP options...
ATMP Mode=Home
Type=Gateway
Password=private
SAP Reply=No
UDP Port=5150
- Close the Ethernet profile.
- Open a Connection profile and configure an IP routing connection to the foreign agent.
For example:
Ethernet
Connections
Station=foreign-agent
Active=Yes
Encaps=MPP
Dial #=555-1213
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=foreign-pw
Send PW=home-pw
IP options...
LAN Adrs=10.65.212.226/24
- Open a Connection profile and configure a nailed WAN link to the home network.
Ethernet
Connections
Station=homenet
Active=Yes
Encaps=MPP
Dial #=N/A
Calling #=N/A
Route IP=Yes
IP options...
LAN Adrs=5.9.8.2/24
Telco options...
Call Type=Nailed
Group=1,2
Session options...
ATMP Gateway=Yes
MAX ATMP Tunnels=0
- Close the Connection profile.
Example home agent in gateway mode (IPX)
To configure the home agent in gateway mode to reach an IPX home network:
- Open Ethernet > Mod Config > Ether Options and verify that the LAN interface has an IP
address (required to communicate with the foreign agent) and can route IPX. For example:
Ethernet
Mod Config
IPX Routing=Yes
Ether options
IP Adrs=10.1.2.3/24
IPX Frame=802.2
IPX Enet #=00000000
For details, see Chapter 9, Configuring IPX Routing.
- Open the ATMP Options subprofile and set ATMP Mode to Home and Type to Gateway.
- Specify the password used to authenticate the tunnel. This must match the
Ascend-Home-Agent-Password attribute of mobile nodes' RADIUS profiles.
- Set SAP Reply to Yes.
ATMP options...
ATMP Mode=Home
Type=Gateway
Password=private
SAP Reply=Yes
UDP Port=5150
- Close the Ethernet profile.
- Open a Connection profile and configure an IP routing connection to the foreign agent.
For example:
Ethernet
Connections
Station=foreign-agent
Active=Yes
Encaps=MPP
Dial #=555-1213
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=foreign-pw
Send PW=home-pw
IP options...
LAN Adrs=10.65.212.226/24
- Open a Connection profile and configure a nailed WAN link that routes IPX to the home
network.
Ethernet
Connections
profile 5...
Station=homenet
Active=Yes
Encaps=MPP
PRI # Type=National (for ISDN PRI lines only)
Dial #=555-1212
Route IPX=Yes
Encaps options...
Send Auth=CHAP
Recv PW=homenet-pw
Send PW=my-pw
IPX options...
IPX RIP=None
IPX SAP=Both
NetWare t/o=30
Telco options...
Call Type=Nailed
Group=1,2
Session options...
ATMP Gateway=Yes
MAX ATMP Tunnels=0
- Close the Connection profile.
Configuring the MAX as an ATMP multi-mode agent
You can configure the MAX to act as both a home agent and foreign agent on a tunnel-by-tunnel basis. Figure 13-4 shows an example network topology with a MAX acting as a home agent for Network B and a foreign agent for Network A.
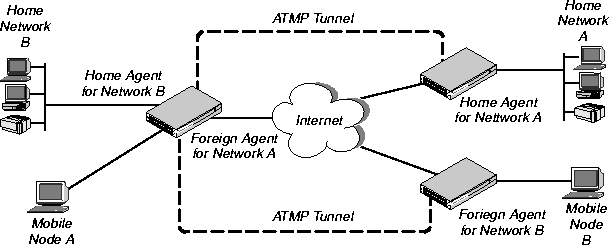
Figure 13-4. MAX acting as both home agent and foreign agent
To configure the MAX as a multi-mode agent, set ATMP Mode to Both and complete both the foreign and home agent requirements. Setting ATMP Mode to Both indicates that the MAX will function as both a home agent and foreign agent on a tunnel-by-tunnel basis.
For example, to configure the MAX to operate as both a home agent and foreign agent:
- Open Ethernet > Mod Config > Ether Options and verify that the LAN interface has an IP
address. For example:
Ethernet
Mod Config
Ether options...
IP Adrs=10.65.212.226/24
- Open the ATMP Options subprofile and set ATMP Mode to Both.
- Configure the other home-agent settings as appropriate; for example, to use Gateway
mode and a password of private:
ATMP options...
ATMP Mode=Both
Type=Gateway
Password=private
SAP Reply=No
UDP Port=5150
To configure the foreign-agent aspect of the multi-mode configuration:
- Open the Auth subprofile and configure RADIUS authentication. For example:
Auth...
Auth=RADIUS
Auth Host #1=10.23.45.11/24
Auth Host #2=0.0.0.0/0
Auth Host #3=0.0.0.0/0
Auth Port=1645
Auth Timeout=1
Auth Key-=[]
Auth Pool=No
Auth Req=Yes
Password Server=No
Password Port=N/A
Local Profile First=No
Sess Timer=0
Auth Src Port=0
Auth Send Attr 6,7=Yes
For more information on each parameter, see the MAX RADIUS Configuration Guide.
- Close the Ethernet profile.
- On the RADIUS server, open the RADIUS user profile and create an entry for a mobile
node. For example:
node1 Password="top-secret"
Ascend-Metric=2,
Framed-Protocol=PPP,
Ascend-IP-Route=Route-IP-Yes,
Framed-Address=200.1.1.2,
Framed-Netmask=255.255.255.0,
Ascend-Primary-Home-Agent=10.1.2.3,
Ascend-Home-Agent-Password="private"
Ascend-Home-Agent-UDP-Port = 5150
Ascend-Home-Network-Name=home-agent
- Close the user profile.
- Open a Connection profile and configure an IP routing connection to the Network A home
agent. For example:
Ethernet
Connections
Station=home-agent
Active=Yes
Encaps=MPP
Dial #=555-1212
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=home-pw
Send PW=foreign-pw
IP options...
LAN Adrs=10.1.2.3/24
- Close the Connection profile.
To configure the home-agent aspect of the multi-mode configuration:
- Open a Connection profile and configure an IP routing connection to the Network B
foreign agent. For example:
Ethernet
Connections
Station=foreign-agent
Active=Yes
Encaps=MPP
Dial #=555-1213
Route IP=Yes
Encaps options...
Send Auth=CHAP
Recv PW=foreign-pw
Send PW=home-pw
IP options...
LAN Adrs=10.65.212.226/24
- Open a Connection profile and configure a nailed WAN link to the Network B home
network.
Ethernet
Connections
Station=homenet
Active=Yes
Encaps=MPP
Dial #=N/A
Calling #=N/A
Route IP=Yes
IP options...
LAN Adrs=5.9.8.2/24
Telco options...
Call Type=Nailed
Group=1,2
Session options...
ATMP Gateway=Yes
MAX ATMP Tunnels=0
- Close the Connection profile.
Supporting mobile node routers (IP only)
To enable an IP router to connect as a mobile node, the foreign agent's RADIUS entry for the mobile node must specify the same netmask as the home network. For example, to connect to a home network whose router has this address:
10.1.2.3/28
The foreign agent's RADIUS entry for the remote router would contain lines like this:
node1 Password="top-secret"
Ascend-Metric=2,
Framed-Protocol=PPP,
Ascend-IP-Route=Route-IP-Yes,
Framed-Address=10.168.6.21,
Framed-Netmask=255.255.255.240,
Ascend-Primary-Home-Agent=10.1.2.3,
Ascend-Home-Agent-Password="private"
With this Framed-Address for the mobile node router (10.168.6.21/28), the connecting LAN can support up to 14 hosts.
The MAX handles routes to and from the mobile node's LAN differently, depending on whether the home agent is configured in router mode or gateway mode.
ATMP connections that bypass a foreign agent
If a home agent MAX has the appropriate RADIUS entry for a mobile node, the mobile node can connect directly to the home agent. An ATMP-based RADIUS entry that is local to the home agent enables the mobile node to bypass a foreign agent connection, but it does not preclude a foreign agent. If both the home agent and the foreign agent have local RADIUS entries for the mobile node, the node can choose between a direct connection or a tunneled connection through the foreign agent.
For example, the following RADIUS entry authenticates a mobile NetWare client that will connect directly to the home agent. In this example, the home agent is configured in gateway mode (it forwards packets from the mobile node across a nailed WAN link to the home IPX network):
mobile-ipx Password = "unit"
User-Service = Framed-User,
Ascend-Route-IPX = Route-IPX-Yes,
Framed-Protocol = PPP,
Ascend-IPX-Peer-Mode = IPX-Peer-Dialin,
Framed-IPX-Network = 40000000,
Ascend-IPX-Node-Addr = 12345678,
Ascend-Home-Agent-IP-Addr = 192.168.6.18,
Ascend-Home-Network-Name = "homenet",
Ascend-Home-Agent-Password = "pipeline"
Note: If the home agent is configured in router mode (in which it forwards packets from the
mobile node to its internal routing module), the Ascend-Home-Network-Name line is not
included in the user entry. The Ascend-Home-Network-Name attribute specifies the name of
the answering unit across the WAN on the home IPX network.
Configuring PPTP tunnels for dial-in clients
PPTP enables Windows 95 and Windows NT Workstation users to dial into a local ISP to connect to a private corporate network across the Internet. To the user dialing the call, the connection looks like a regular login to an NT server, which may support TCP/IP, IPX, or other protocols.
The MAX acts as a PAC (PPTP Access Controller), which functions as a front-end processor to offload the overhead of communications processing. At the other end of the tunnel, the NT server acts as a PNS (PPTP Network Server). All authentication is negotiated between the Windows 95 or NT client and the PNS. The NT server's account information remain the same as if the client dialed in directly; no changes needed.
How the MAX works as a PAC
Currently, PPTP supports call routing and routing to the NT server by PPP-authenticated connection on a per-line basis, or on the basis of called number or calling number. The following section describes how to dedicate an entire WAN access line for each destination PNS address. For details on configuring WAN lines and assigning phone numbers, see Chapter 2, Configuring the MAX for WAN Access. For details on routing PPTP calls on the basis of called or calling number, see the MAX RADIUS Configuration Guide.
In the PPTP configuration, you specify the destination IP address of the PNS (the NT server), to which all calls that come in on the PPTP-routed line will be forwarded. When the MAX receives a call on that line, it passes the call directly to the specified IP address end-point, creating the PPTP tunnel to that address if one is not already up. The PNS destination IP address must be accessible via IP routing.
Note: The MAX handles PPTP calls differently than regular calls. No Connection profiles are
used for these calls, and the Answer profile is not consulted. They are routed through the PPTP
tunnel based solely upon the phone number dialed.
These are the parameters related to a PPTP PAC configuration:
Ethernet
Mod Config
L2 Tunneling Options...
PPTP Enabled=Yes
Line 1 tunnel type=PPTP
Route line 1=10.65.212.11
Line 2tunnel type=None
Route line 2=0.0.0.0
Line 3tunnel type=None
Route line 3=0.0.0.0
Line 4tunnel type=None
Route line 4=0.0.0.0
For more information on each parameter, see the MAX Reference Guide.
Understanding the PPTP PAC parameters
This section provides some background information about configuring PPTP.
Enabling PPTP
When you enable PPTP, the MAX can bring up a PPTP tunnel with a PNS and respond to a request for a PPTP tunnel from a PNS. You must specify the IP address of the PNS in one or more of the Route Line parameters.
Specifying a PRI line for PPTP calls and the PNS IP address
The PPTP parameters include four Route Line parameters, one for each of the MAX unit's WAN lines. If you specify the IP address of a PNS in one of these parameters, that WAN line is dedicated to receiving PPTP connections and forwarding them to that destination address.
The IP address you specify must be accessible via IP, but there are no other restrictions on it. It can be across the WAN or on the local network. If you leave the default null address, that WAN line handles calls normally.
Example PAC configuration
Figure 13-6 shows an ISP POP MAX unit communicating across the WAN with an NT Server at a customer premise. Windows 95 or NT clients dial into the local ISP and are routed directly across the Internet to the corporate server.
In this example, the MAX unit's fourth WAN line is dedicated to PPTP connections to that server.
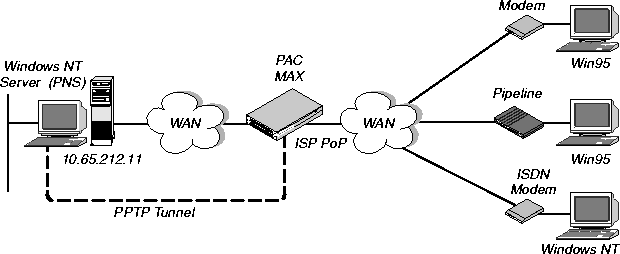
Figure 13-5. PPTP tunnel
To configure this MAX for PPTP:
- Open Ethernet > Mod Config > PPTP Options.
- Turn on PPTP, and specify the PNS IP address next to Route Line 4.
Ethernet
Mod Config
L2 Tunneling Options...
PPTP Enabled=Yes
Line 1 tunnel type=None
Route line 1=0.0.0.0
Line 2tunnel type=None
Route line 2=0.0.0.0
Line 3tunnel type=None
Route line 3=0.0.0.0
Line 4tunnel type=PPTP
Route line 4=10.65.212.11
- Close the Ethernet Profile.
Example PPTP tunnel across multiple POPs
Figure 13-5 shows an ISP POP MAX communicating through an intervening router to the PNS that is the end-point of its PPTP tunnel. The MAX route the packets in the usual way to reach the end-point IP address.
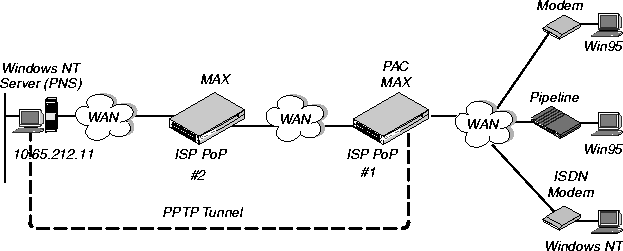
Figure 13-6. PPTP tunnel across multiple POPs
In this example, the MAX at ISP POP #1 dedicates its second WAN line to PPTP connections to the PNS at 10.65.212.11. To configure this MAX as a PAC:
- Open Ethernet > Mod Config > PPTP Options.
- Turn on PPTP, and specify the PNS IP address next to Route Line 2.
Ethernet
Mod Config
L2 Tunneling Options...
PPTP Enabled=Yes
Line 1 tunnel type=None
Route line 1=0.0.0.0
Line 2tunnel type=PPTP
Route line 2=10.65.212.11
Line 3tunnel type=None
Route line 3=0.0.0.0
Line 4tunnel type=None
Route line 4=0.0.0.0
- Close the Ethernet Profile.
The PAC must have a route to the destination address, in this case a route through the ISP POP #2. This does not have to be a static route, it can be learned dynamically via routing protocols. This example shows a static route to ISP POP #2:
- Open an unused IP Route profile and activate it.
Ethernet
Static Rtes
Name=pop2
Active=Yes
- Specify the PNS destination address.
Dest=10.65.212.11
- Specify the address of the next-hop router (ISP POP #2), for example:
Gateway=10.1.2.4
- Specify a metric for this route, the route's preference, and whether the route is private. For
example:
Metric=1
Preference=100
Private=Yes
- Close the IP Route profile.
Routing a terminal-server session to a PPTP server
You can initiate a PPTP session via the terminal-server interface, which routes the session to a PPTP server. The PPTP command gives you two options for selecting the tunnel the MAX creates. You can specify either the IP address or host name of the PPTP server. Normal PPTP authentication proceeds once the MAX creates the tunnel.
To use the command, enter the following at the terminal-server prompt:
pptp pptp_server
where pptp_server is the IP address or hostname of the PPTP server. When you enter the command, the system displays the following text:
PPTP: Starting session
PPTP Server pptp_server
Configuring L2TP tunnels for dial-in clients
L2TP enables you to dial into a local ISP and connect to a private corporate network across the Internet. You dial into a local MAX, configured as an L2TP Access Concentrator (LAC), and establish a PPP connection. Attributes in your RADIUS user profile specify that the MAX, acting as an LAC, establish an L2TP tunnel. The LAC contacts the L2TP Network Server (LNS), which is connected to the private network. The LAC and the LNS establish an L2TP tunnel (via UDP), and any traffic your client sends is tunneled to the private network. Once the MAX units establish the tunnel, the client connection has a PPP connection with the LNS, and appears to be directly connected to the private network.
You can configure the MAX to act as either an LAC, an LNS, or both. The LAC performs the following functions:
- Establishes PPP connections with dial-in clients.
- Sends requests to LNS units requesting creation of tunnels.
- Encapsulates and forwards all traffic from clients to the LNS via the tunnel.
- De-encapsulates traffic received from an established tunnel, and forwards it to the client.
- Sends tunnel-disconnect requests to LNS units when clients disconnect.
The LNS performs the following functions:
- Responds to requests by LAC units for creation of tunnels.
- Encapsulates and forwards all traffic from the private network to clients via the tunnel.
- De-encapsulates traffic received from an established tunnel, and forwards it to the private network.
- Disconnects tunnels on the basis of requests from the LAC.
- Disconnects tunnels on the basis of expiration of the value you set for a user profile's MAX-Connect-Time attribute. You can also manually disconnect tunnels from the LNS via SNMP, the terminal-server Kill command, or the DO Hangup command (which you access by pressing <control> D).
Note: With this release, a MAX acting as an LNS cannot send Incoming Call Requests to an
LAC. Only an LAC can make requests for the creation of L2TP tunnels.
Configuring L2TP tunneling
This section describes how L2TP tunnels work between an LAC and an LNS. A client dials into an LAC, from either a modem or ISDN device, and the LAC establishes a cross-Internet IP connection to the LNS. The LAC then requests an L2TP tunnel via the IP connection.
The LNS is the terminating part of the tunnel, where most of the L2TP processing occurs. It communicates with the private network (the destination network for the dial-in clients) through a direct connection.
Figure 13-7 shows an ISP POP MAX, acting as an LAC, communicating across the WAN with a private network. Clients dial into the ISP POP and are forwarded across the Internet to the private network.
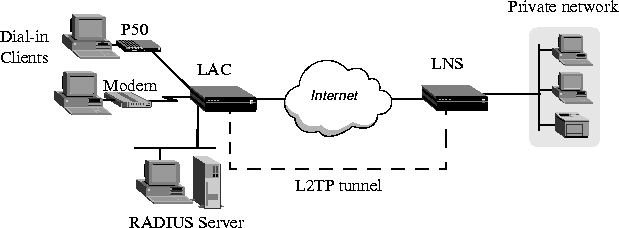
Figure 13-7. L2TP tunnel across the Internet
How the MAX creates L2TP tunnels
The dial-in client, the LAC, and the LNS establish, use and terminate an L2TP-tunnel connection as follows:
- A client dials, over either a modem or ISDN connection, into the LAC.
- On the basis of dialed number or after authentication (depending on the LAC
configuration), the LAC communicates with the LNS to establish an IP connection.
- Via the IP connection, the LAC and LNS establish a control channel.
- The LAC sends an Inbound Call Request to the LNS.
- Depending on the LNS configuration, the client might need to authenticate itself a second
time.
- After successful authentication, the tunnel is completed, and data traffic flows.
- When the client disconnects from the LAC, the LAC sends a Call Disconnect Notify
message to the LNS. The LAC and LNS disconnect the tunnel.
LAC and LNS mode
The MAX can function as an LAC, an LNS, or both. When configured as both, the MAX acts an LAC on the basis of the dial-in client configuration. The MAX acts as an LNS when it receives an Inbound Call Request from an LAC.
Note: The MAX can support several simultaneous connections, some where it acts an LAC,
and some where it acts as an LNS. For any single connection, however, the MAX can operate
as either an LAC or LNS, but not both.
Authentication
Either the LAC, the LNS, or both, can perform PAP or CHAP authentication of clients for which they create tunnels. If you configure the MAX to create tunnels on a per-line basis, only the LNS can perform authentication, because the MAX automatically builds a tunnel to the LNS for any call it that it receives on that line.
If you use RADIUS to configure L2TP on a per-user basis, and specify the Client-Port-DNIS attribute, the LAC does not perform PAP or CHAP authentication. When use specify Client-Port-DNIS, the tunnel is created as soon as the LAC receives the DNIS number and it matches a Client-Port-DNIS for any user profile. You can configure the LNS to perform PAP or CHAP authentication after the LAC and LNS establish the tunnel.
If you use RADIUS to configure L2TP, but do not specify the Client-Port-DNIS attribute, the LAC performs PAP or CHAP authentication before the tunnel is established. Once the tunnel is up, the LNS can perform authentication again on the client. Each client sends the same username and password during the authentication phase, so for each client, make sure you configure the LAC and LNS to look for the same usernames and passwords.
You can also direct the MAX to create an L2TP tunnel, from the terminal server, by using the L2TP command. You can configure authentication on the LNS, requiring users to authenticate themselves when they manually initiate L2TP tunnels from the terminal server.
Configuring the MAX as an LAC
The LAC is responsible for requesting L2TP tunnels to the LNS. You configure the LAC to determine when a dial-in connection should be tunneled, and you can specify the LNS used for the connection.
Understanding the L2TP LAC parameters
This section provides some background information about parameters used in configuring the MAX as an LAC:
Configuring the MAX as an LAC
To configure the MAX as an L2TP LAC, you must first enable L2TP LAC on the MAX, then configure how the MAX determines which connections are tunneled.
Configuring system-wide L2TP LAC parameters
To configure system-wide L2TP LAC parameters on the MAX:
- Open the Ethernet > Mod Config > L2 Tunneling options menu.
- Set L2TP Enabled to either LAC or Both.
Enabling L2TP tunneling for an entire WAN line
If you want the LAC to create L2TP tunnels for every call received on a specific WAN line:
- Open the Ethernet > Mod Config > L2 Tunneling options menu.
- For the line for which you are configuring LAC functionality (Line n), set Line n tunnel
type to L2TP. For example, if you want to tunnel all calls received on the first WAN port
(labelled WAN 1 on the MAX backpanel), set Line 1 tunnel type=L2TP.
- Set Route line n to the IP address of the LNS.
Enabling L2TP tunneling on a per-user basis
You can configure RADIUS to direct the MAX to create L2TP tunnels for specific users. To do so, you use three standard RADIUS attributes: Tunnel-Type, Tunnel-Medium-Type, and Tunnel-Server-Endpoint. Table 13-3 describes these attributes.
Table 13-3. RADIUS attributes for specifying L2TP tunnels
Attribute
|
Description
|
Possible values
|
|---|
|
Tunnel-Type (64)
|
Specifies which tunneling protocol to use for this connection.
|
PPTP or L2TP
You must set this attribute to L2TP to direct the MAX to create an L2TP tunnel.
|
|
Tunnel-Medium-Type (65)
|
Specifies the protocol type, or medium, used for this connection. Currently, the MAX supports IP only. Future software releases will support additional medium types.
|
Currently, the only supported value is IP. You must set this attribute to IP.
|
|
Tunnel-Server-Endpoint (67)
|
Specifies the IP address or fully qualified host name of the LNS, if you set Tunnel-Type to L2TP, or PPTP Network Server (PNS), if you set Tunnel-Type to PPTP.
|
If a DNS server is available, you can specify the fully-qualified host name of the LNS, Otherwise, specify the IP address of the LNS in dotted decimal notation n.n.n.n, where n is a number from 0 to 255. You must set this attribute to an accessible IP host name or address.
|
Configuring the MAX as an LNS
When MAX acts as an LNS, it responds to requests by LAC units to establish tunnels. The LNS does not initiate outgoing requests for tunnels, so the configuration of MAX is simple. Proceed as follows:
- Open the Ethernet > Mod Config > L2 Tunneling options menu.
- Set L2TP Enabled to either LNS or Both.
![[Top]](../../images/home.jpg)
![[Contents]](../../images/contents.jpg)
![[Prev]](../../images/previous.jpg)
![[Next]](../../images/next.jpg)
![[Last]](../../images/index.jpg)


techpubs@eng.ascend.com
Copyright © 1998, Ascend Communications, Inc. All rights
reserved.




